First, I was able to successfully setup a letsencrypt certificate on an Ubuntu 14.0.4 server for my domain, and I confirmed everything was okay, by verifying I could access my domain via https and checking that I really did have the correct files in:
/etc/letsencrypt/live/domain.tld/
I have a Xeams mail server running on the server and I've been finding it difficult following the steps in the guide. First I had to convert the cert files generated by LetsEncrypt from .pem to .crt using:
openssl x509 -outform der -in my-cert.pem -out my-cert.crt
Which worked fine and converted the files successfully, but the problem I have with the guide is that, It assumes I don't already have an ssl certificate which isn't the case. I don't think I should have to generate a CSR code again when I already have the certificate from Letsencrypt.
To be clear, these are the cert files I have for my domain.
- cert.pem
- chain.pem
- privkey.pem
- fullchain.pem
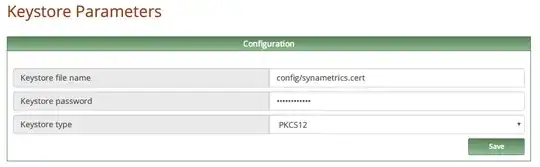
But in the guide, it requires me generating CSR codes and whatnot, I have skipped generating a CSR to the part where I have to add the certificates to the keystore, but Its not very straightforward what I'm supposed to do, cause the files in the guide aren't correlating with what I have gotten from Letsencrypt.
When I try to follow the rest of the guide, and test that my server accepts connections on Secure IMAP port: 995 , my server returns a self signed certificate and not the certificate from the CA.
I used openssl to test the secure IMAP port 995
openssl s_client -connect localhost:995
I also confirmed Letsencrypt support for ssl email protocols and Java, so there has to be something I am not getting right. I have not been able to figure out how to add my certificates to the keystore.