For the better part of yesterday (and today so far) my server is being attacked with brute force.
I am rather an inexperience admin when it gets passed the basics. I understand how to find things, sometimes understand how to configure things. This attack has got me stressed and tired now.
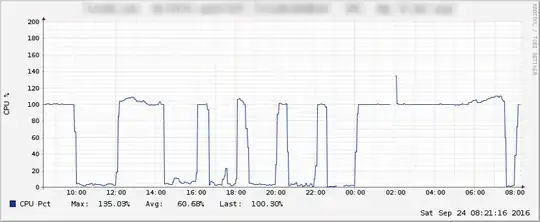
Every time I think I got it, it comes back. Here is my CPU usage for the las 24 hours.
It initialized as an xmlrpc attack with some WordPress sites, I've since disabled that with some plugins - I've also removed the files themselves.
The attacks continue. My auth.log show a lot of attempts. I did some reading, could fail2ban is a great tool for stopping brute force attacks.
Configured it - I think it's right even though there are some "Command not found" errors - it says it banned an IP that was attacking me.
Things are quiet for now. I check this morning - CPU cranked up. I run top to see whats taking up all the APU the program 'host' is running.
4274 forge 20 0 1721620 6760 3264 S 98.8 0.3 14:04.99 host
4537 forge 20 0 362804 33656 8664 R 0.3 1.6 0:00.14 php5-fpm
1 root 20 0 33504 3968 2624 S 0.0 0.2 0:01.48 init
2 root 20 0 0 0 0 S 0.0 0.0 0:00.00 kthreadd
3 root 20 0 0 0 0 S 0.0 0.0 0:00.06 ksoftirqd/0
5 root 0 -20 0 0 0 S 0.0 0.0 0:00.00 kworker/0:0H
6 root 20 0 0 0 0 S 0.0 0.0 0:00.10 kworker/u2:0
It even says by my user. Something else is running this - how can I find out?