Use Encryption for Data
Specifies whether data should be encrypted before sending it over the network.
The valid values are "true" and "false". The default value is "false".
As Microsoft notes, that has a number of issues:
- it requires obtaining a valid SSL certificate
- it requires installing the SSL certificate on the server
- it requires altering the connection string
- it's not what i'm asking
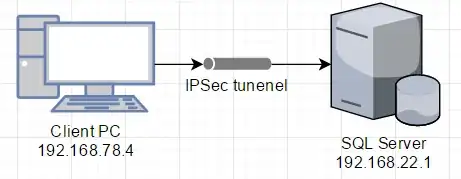
IPSec
Fortunately, Microsoft suggests that IPSec can be used as an alternative:
SQL Server data can be encrypted during transmission by using IPSec. IPSec is provided by the client and server operating systems and requires no SQL Server configuration. For information about IPSec, see your Windows or networking documentation.
Because even though both the client and server are on the same Local Area Network:
We don't want anyone with WireShark, a hub, a PC in permiscuious mode, or a switch that can monitor traffic able to see the traffic.
The question is: how do you do it?
Research Effort is Immaterial
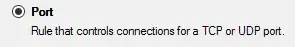
On the client machine, we want to configure a policy that requires IPSec connection to an SQL Server (e.g. port 1433). From within Windows Firewall with Advanced Security:
Create a new outbound firewall rule
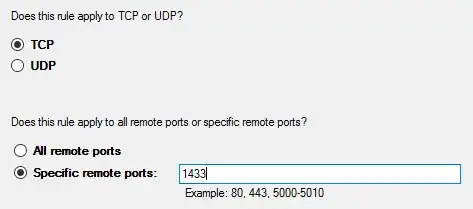
for an IP port:
for destination TCP port 1433
Allow the connection, if it is secure
Finish
The downside is that the client now cannot connect to the server:
Bonus Reading
- Superuser - Windows 7 - How to use IPSec (refers to tunnel mode)
- Technet: Encrypting Connections to SQL Server (refers users to use IPSec)
- MS Forums: IPSec to secure SQL Server Connection (accepted answer says he gave up trying to use IPsec)
- How do I encrypt SQL Server traffic with IPSEC? (accepted answer doesn't indicate how to encrypt SQL Server traffic with IPSec)
- Serverfault user Greg says you can't use IPSec to encrypt network traffic
- IPSec for LAN traffic: Basic considerations? (general discussion of encrypting LAN traffic)