I am exploring CentOS as a possibility for hosting a number of servers (mail, web, database, etc). Each machine will have a single purpose, and security is a priority.
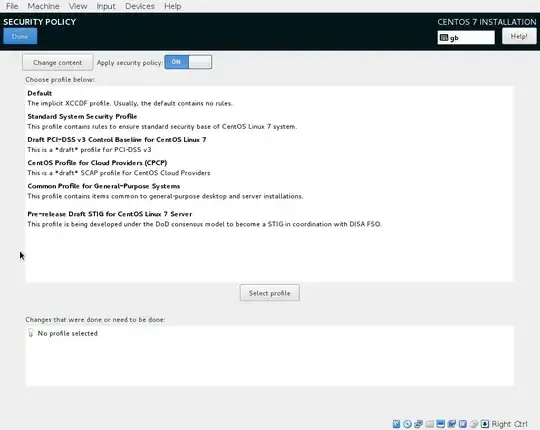
At the first installation, I am confronted with this:
Information about these policies is here but it's a bit overwhelming. Also if you drill into it you see things like
To ensure the system can cryptographically verify base software packages come from Red Hat (and to connect to the Red Hat Network to receive them), the Red Hat GPG key must properly be installed.
Presumably not all such things translate exactly to CentOS, but I'm an Ubuntu user so I don't really understand the extent of the equivalence.
It seems that these security profiles are created as a matter of legal compliance, audits, and business concerns foremost, rather than being defined strictly in terms of security itself.
What's the best option for "I'm not exactly sure what I'm doing just get but for now I want to be paranoid"?
As well as each server instance having a single function, they will be non-graphical terminals with ssh access.