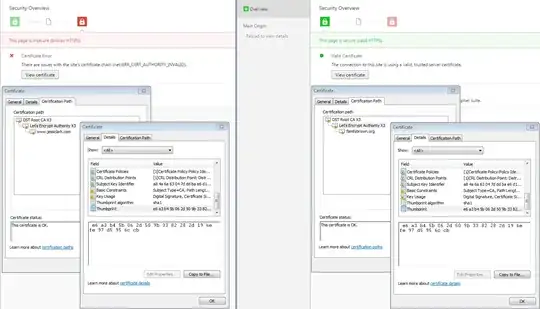
Why does Chrome trust the certificate authority for this site, but not for this one?
This is the same machine, same browser, signed by the same authority, and Chrome shows the intermediate chain signed by the same root CA.
You can confirm the host does not serve the intermediate CA chain as is reported by Tim's answer via services like sslshopper and digicert by manually downloading and verifying it with openssl
openssl s_client -showcerts -connect www.jessclark.com:443
However the full chain does clearly appear in Chrome details when examining the certificate, yet crazily enough it still doesn't trust the authority even though it recognizes it. Because the intermediate chain is missing, then I would expect it to only show www.jessclark.com and not the Let's Encrypt cert linked to DST Root CA X3.
I'm using Google Chrome Version 50.0.2661.102 m on Windows 7
Click the image to view full resolution screenshot.
Interestingly, the authority is trusted in other browsers like Chromium Version 51.0.2704.79 Ubuntu 16.04 (64-bit), Internet Exploder 11 Windows 7, and reportedly by others as well in the comments. Firefox does seem to strictly reject it the most.