I asked this on the AWS forum but not getting much traction. My root problem is that I'm trying to restore a MS SQL Server RDS database and getting the error message "Database backup/restore option is not enabled yet or is in the process of being enabled. Please try again later." I found this thread about this problem:
https://forums.aws.amazon.com/message.jspa?messageID=736361
Which suggests to add an option to the database's option group. However, the "Add Option" button on the option group is disabled, and the drop-down to select an option group for the database is also disabled. So I can't add an option to the option group, and I can't make a new option group and choose that. I learned that you cannot add options to a default option group, so I definitely need to create an option group. I still don't know why I can't change the option group of an existing RDS instance.
So I made a new option group, no problem. I made a brand new RDS instance so I could pick a different option group. On the new option group I created I can click Add Option, but can't successfully complete the process. I created an IAM role with the RDS full access permission, and when attempting to add the backup/restore option with that role to the option group, I get this:
"IAM role ARN value is invalid or does not include the required permissions for: SQLSERVER_BACKUP_RESTORE (Service: AmazonRDS; Status Code: 400; Error Code: InvalidParameterValue; Request ID: 3824d081-648a-11e6-9c94-87e171d2e1f8)"
I don't know a lot about IAM so I'm not sure what to do with this. Ideas?
UPDATE
I got another response on the AWS forum. Here's the suggestion and my results.
Please try the following steps -
- Select Option Groups from the left hand side panel in RDS Console
- Select the Option group you created and click on the Add Option button
- Select SQL_SERVER_BACKUP_RESTORE in the Option drop-down.
- Click the text Create a New Role under the IAM Role drop-down. This will show you options for IAM Role creation.
- Add a name for the IAM Role, select the S3 bucket you want to use and check Yes for the Apply Immediately radio button.
- Click the Add Option button.
Reply
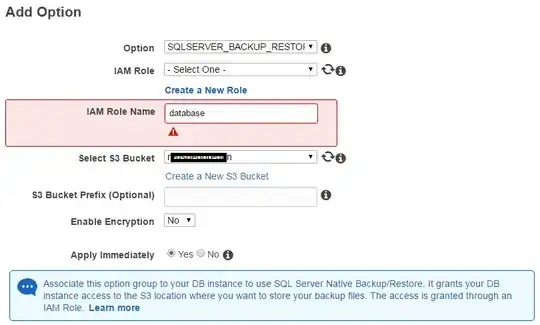
That sounded good! But after I click Add Option at the bottom of the form, the button disabled for a few seconds and then the IAM Role Name field was surrounded by red. I've attached a screenshot. Clicking on the exclamation mark or anywhere in the red doesn't bring up any additional information. I've tried a couple of different names with the same result. Are there rules about the name that the page doesn't specify? Thanks again for your help.