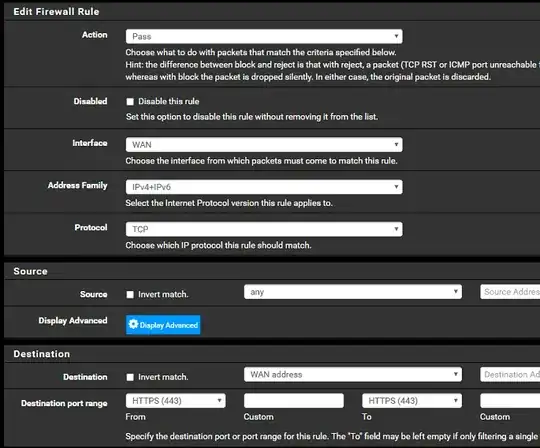
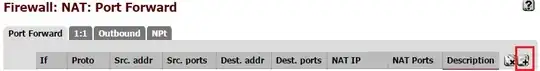
I've included my current setup.
However, when I try and access the firewall from outside my organization, I only get this:
ERR_CONNECTION_TIMED_OUT
Am I not the correct protocols through?
EDIT:
(not mentioned is above this ruleset I back a default catch and block ALL for ALL protocols thinking that I set a block all then allow on a case by case basis.)
So I narrowed down the issue... I think. Apparently, it works fine if you leave the protocol blocked to TCP/UDP. But the moment you try and block ALL protocols it seems to also break OpenVPN and HTTPS.
Maybe I need to allow one of the other protocols as well?