The SSL certificate is trusted on most Desktop computers, but only some Android devices. However, even on Android devices where the certificate is untrusted, the root certificate is installed.
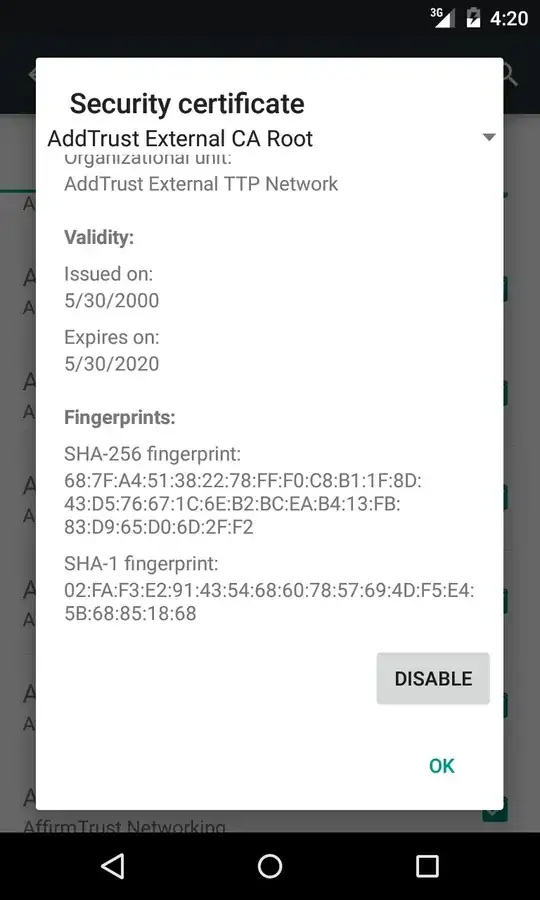
I must have tried a hundered ways of resolving this problem, but I think it has something to do with the AddTrust External CA Root (perhaps to do with the SHA-256 fingerprint, which is missing?).
- The cause does not appear to be an incorrect Certificate Authority Bundle.
- The cause does not appear to be related to time.
- All online SSL checker tools I've used (e.g., https://www.ssllabs.com) say the SSL certificate is installed correctly.
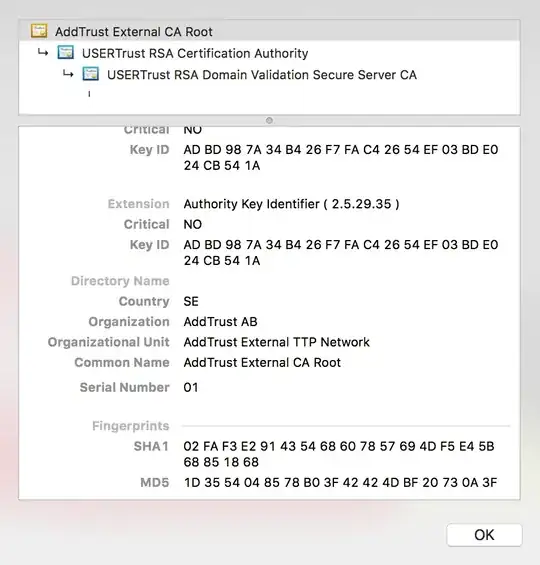
- The root certificate is located on my Android device and on my Desktop computer (see the SHA1 fingerprint in the two screenshots, which is identical).
EDIT 1
I believe I have included the new intermediary certificate in my certificate chain, but SSL labs is still reporting that it's not present (even after clicking the "Clear cache" button).
EDIT 2
To be explicit about what I've done:
I've signed into to WHM and clicked the "Install an SSL Certificate on a Domain" option.
I've entered the domain name "www.angusaustralia.com.au".
I've entered the IP address "27.124.127.2".
I've entered the certificate issued to me.
-----BEGIN CERTIFICATE----- MIIFnDCCBISgAwIBAgIRAP/vaD7B7JaVJvqC2H7jiDcwDQYJKoZIhvcNAQELBQAw gZMxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpOZXcgSmVyc2V5MRQwEgYDVQQHEwtK ZXJzZXkgQ2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBOZXR3b3JrMTkwNwYD VQQDEzBVU0VSVHJ1c3QgUlNBIERvbWFpbiBWYWxpZGF0aW9uIFNlY3VyZSBTZXJ2 ZXIgQ0EwHhcNMTYwNjI3MDAwMDAwWhcNMTcwNjI3MjM1OTU5WjCBhzEhMB8GA1UE CxMYRG9tYWluIENvbnRyb2wgVmFsaWRhdGVkMScwJQYDVQQLEx5Ib3N0ZWQgYnkg Q3JhenkgRG9tYWlucyBGWi1MTEMxFTATBgNVBAsTDEVzc2VudGlhbFNTTDEiMCAG A1UEAxMZd3d3LmFuZ3VzYXVzdHJhbGlhLmNvbS5hdTCCASIwDQYJKoZIhvcNAQEB BQADggEPADCCAQoCggEBALbDVHckJORMdY0/ygZqo0jjI02E883VpyL0RCeq7wuI wkCWys3L1v6ZjW45wBEbsYGwpZMV3/IdXYTc5cO5ke4bYnXP4y5NbteVvNOQi1sX FMf8DlpJ+K0ZRcWQVIpsSIRRslXUPw4PWu27Q6Sgp1JuVa2YhXu7hSshIrIhkslT Bx/IL67ZZfwo3wpMoig271yGHT4y1KAz9BfLTqVftL8n7uCKYFj3vo5E44czqSRl wYdQgSOLUc1G7jt33fCV8t+hXbKR0WdutTwdBQfftp2ZCSYwKCgCl3yDSLnqbbI+ 8GdFuLM4c1ZZwbFfJiKSZ5qDBg0IeODgIRdxSDmirDECAwEAAaOCAfMwggHvMB8G A1UdIwQYMBaAFKbB5+H09kdj1y99jZD4uiNPYKyeMB0GA1UdDgQWBBRbjv4H+sED CnGTcCoBdTIGeUPOOjAOBgNVHQ8BAf8EBAMCBaAwDAYDVR0TAQH/BAIwADAdBgNV HSUEFjAUBggrBgEFBQcDAQYIKwYBBQUHAwIwTAYDVR0gBEUwQzA3BgwrBgEEAbIx AQIBAwQwJzAlBggrBgEFBQcCARYZaHR0cHM6Ly9jcHMudXNlcnRydXN0LmNvbTAI BgZngQwBAgEwWAYDVR0fBFEwTzBNoEugSYZHaHR0cDovL2NybC51c2VydHJ1c3Qu Y29tL1VTRVJUcnVzdFJTQURvbWFpblZhbGlkYXRpb25TZWN1cmVTZXJ2ZXJDQS5j cmwwgYoGCCsGAQUFBwEBBH4wfDBTBggrBgEFBQcwAoZHaHR0cDovL2NydC51c2Vy dHJ1c3QuY29tL1VTRVJUcnVzdFJTQURvbWFpblZhbGlkYXRpb25TZWN1cmVTZXJ2 ZXJDQS5jcnQwJQYIKwYBBQUHMAGGGWh0dHA6Ly9vY3NwLnVzZXJ0cnVzdC5jb20w OwYDVR0RBDQwMoIZd3d3LmFuZ3VzYXVzdHJhbGlhLmNvbS5hdYIVYW5ndXNhdXN0 cmFsaWEuY29tLmF1MA0GCSqGSIb3DQEBCwUAA4IBAQCfA2SHg1DtKmHvipfT3REv yowcSTu7/PbKsOAnxdFlnfziKImPJcAwR7PWQoAFAG3pqfk0lGpxkeXN4UhXRs6m MlKKy1xY5H8B4hytCAQDzfZGx0lL4ajeLDsZ439YsHR33abhkf6IieHG412x6PkO csr8NFqevOnxAXkjV4yvfQIPk8sGkzT4rdIlMAS7ZW39wKGe31rYrHFXo1EJqswE mFjMfYtteExXW1e5RqNyecYZ/A8mkJduqiMNvpEzAtDVzKh49bxB4gI97UsIfA9G 4k2KzJArfl+gUFucAIPWEwO2ljXMgOmHCtuTycUmir2KDg5OIDzv7M5snwMVNQs7 -----END CERTIFICATE-----
I've entered the private key (not listed below).
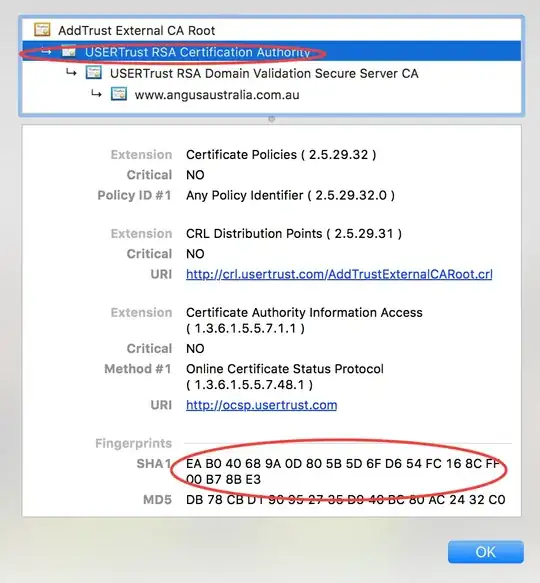
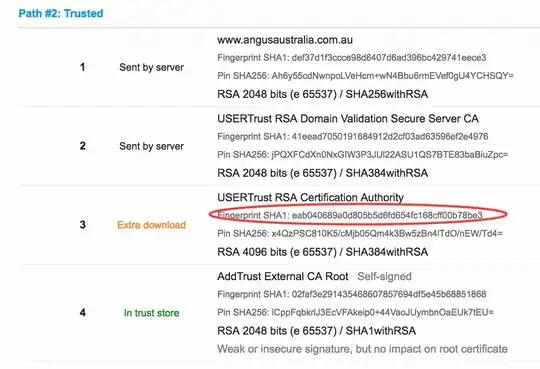
I've entered the following certificate key chain (many combinations of the below, but I believe this "longer" keychain should work, as per the discussion on the SSLLabs website). This keychain includes the older "USERTrust RSA Certification Authority", which should be trusted by older devices.
-----BEGIN CERTIFICATE----- MIIGFzCCA/+gAwIBAgIQckB41CE86gO/FOVeP1YCNzANBgkqhkiG9w0BAQwFADCBiDELMAkGA1UE BhMCVVMxEzARBgNVBAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0plcnNleSBDaXR5MR4wHAYDVQQK ExVUaGUgVVNFUlRSVVNUIE5ldHdvcmsxLjAsBgNVBAMTJVVTRVJUcnVzdCBSU0EgQ2VydGlmaWNh dGlvbiBBdXRob3JpdHkwHhcNMTQwODIyMDAwMDAwWhcNMjkwODIxMjM1OTU5WjCBkzELMAkGA1UE BhMCVVMxEzARBgNVBAgTCk5ldyBKZXJzZXkxFDASBgNVBAcTC0plcnNleSBDaXR5MR4wHAYDVQQK ExVUaGUgVVNFUlRSVVNUIE5ldHdvcmsxOTA3BgNVBAMTMFVTRVJUcnVzdCBSU0EgRG9tYWluIFZh bGlkYXRpb24gU2VjdXJlIFNlcnZlciBDQTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB AMTDft1Zl+V3Koj2wygf++oaX4pvUTmt0zbGzThksBeNYpMzdR1ahJz9RSsMTsRMuichj06TmJbi 91hvyjuX8jrq1Ep0dS27m9ZgVNToCltsxAj8diDPs/UyAwMiLCPKldQMf4h0Gnii3pWtKJlJw09O CqiEmFdJg1DXbRFG5N5iSO4fyKAtD4aDEo+BY1qi+uT3X/RzO+T73WO0BpZGL6OH4sVXhKFY+z6q t22LbsTT2vH0rlFyYav9iZFuZlM0rUYMcLJm9yU8L659pwVdAo0YVfv3x42QsQF9W7qNGCndhHNI ehLGpV7j2KwaBKq9GFD8BxcpxjUAMhuESdWDa80CAwEAAaOCAW4wggFqMB8GA1UdIwQYMBaAFFN5 v1qqK0rPVIDh2JvAnfKyA2bLMB0GA1UdDgQWBBSmwefh9PZHY9cvfY2Q+LojT2CsnjAOBgNVHQ8B Af8EBAMCAYYwEgYDVR0TAQH/BAgwBgEB/wIBADAdBgNVHSUEFjAUBggrBgEFBQcDAQYIKwYBBQUH AwIwGwYDVR0gBBQwEjAGBgRVHSAAMAgGBmeBDAECATBQBgNVHR8ESTBHMEWgQ6BBhj9odHRwOi8v Y3JsLnVzZXJ0cnVzdC5jb20vVVNFUlRydXN0UlNBQ2VydGlmaWNhdGlvbkF1dGhvcml0eS5jcmww dgYIKwYBBQUHAQEEajBoMD8GCCsGAQUFBzAChjNodHRwOi8vY3J0LnVzZXJ0cnVzdC5jb20vVVNF UlRydXN0UlNBQWRkVHJ1c3RDQS5jcnQwJQYIKwYBBQUHMAGGGWh0dHA6Ly9vY3NwLnVzZXJ0cnVz dC5jb20wDQYJKoZIhvcNAQEMBQADggIBAELQvN4Fo+l0anb2ajsD/Baf/7IsyDmPEmfYADO2mpz3 QWmEOsuc2/jbHyLoryNQq9PHUSngzRmfe7N+iFfqF5p8/sbFUbwQrN4e5yXDagrFakztUlxFXR73 fwIk5Rc9KmIDudq7yqzN68To4sbUpzopPg76AKejfkb3Y8V0yEm2TMsFP2W7d8S6O74TO4PpfR3Q Ef5KItzX6cWubJ7e2dpRXMaocoLTzTX8ZJlP52/lUN/ALjMOga4aZkRIMY0S1X8w1ywERvkcm63Q ZnXROlOHmK8cGlHrKaenPnxkipEXhRWoNvlTVVBTH8CjDsaNN+jPMij+feO6mLvXYlNieyW2YU6/ G7lMYVNIDczcFby6xUu1pHuDUAmyS0Qn2snHrevLaFzh60jQ/gfmWO2K2vtwhFQDnUF/dq7M8tfB vF2g/8yHDsZIJ1t4PGW6sFfqczJhwEf6LdNn/D/ealgg+IYdixjChRsMd1CaavxPXfD6k7U4aX91 sL25B8zQn5/yTpTq0oKTJQgsaQSmB6OYkS8dUIW7Q9XLmSboySMzBNK6MPW24hAsYx2gGTOM1Xtl o/V515Q4HCaMS6OhVNGJnncATAT/a7FiMeWxe3shQ2pVT4dfiHkHB92qGrLc/aVFJ1lo+vqB4aqk ILjAI7MLPZQY2MnnThQyv6WWAcpxZi4H -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- MIIFdzCCBF+gAwIBAgIQE+oocFv07O0MNmMJgGFDNjANBgkqhkiG9w0BAQwFADBvMQswCQYDVQQG EwJTRTEUMBIGA1UEChMLQWRkVHJ1c3QgQUIxJjAkBgNVBAsTHUFkZFRydXN0IEV4dGVybmFsIFRU UCBOZXR3b3JrMSIwIAYDVQQDExlBZGRUcnVzdCBFeHRlcm5hbCBDQSBSb290MB4XDTAwMDUzMDEw NDgzOFoXDTIwMDUzMDEwNDgzOFowgYgxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpOZXcgSmVyc2V5 MRQwEgYDVQQHEwtKZXJzZXkgQ2l0eTEeMBwGA1UEChMVVGhlIFVTRVJUUlVTVCBOZXR3b3JrMS4w LAYDVQQDEyVVU0VSVHJ1c3QgUlNBIENlcnRpZmljYXRpb24gQXV0aG9yaXR5MIICIjANBgkqhkiG 9w0BAQEFAAOCAg8AMIICCgKCAgEAgBJlFzYOw9sIs9CsVw127c0n00ytUINh4qogTQktZAnczomf zD2p7PbPwdzx07HWezcoEStH2jnGvDoZtF+mvX2do2NCtnbyqTsrkfjib9DsFiCQCT7i6HTJGLSR 1GJk23+jBvGIGGqQIjy8/hPwhxR79uQfjtTkUcYRZ0YIUcuGFFQ/vDP+fmyc/xadGL1RjjWmp2bI cmfbIWax1Jt4A8BQOujM8Ny8nkz+rwWWNR9XWrf/zvk9tyy29lTdyOcSOk2uTIq3XJq0tyA9yn8i NK5+O2hmAUTnAU5GU5szYPeUvlM3kHND8zLDU+/bqv50TmnHa4xgk97Exwzf4TKuzJM7UXiVZ4vu PVb+DNBpDxsP8yUmazNt925H+nND5X4OpWaxKXwyhGNVicQNwZNUMBkTrNN9N6frXTpsNVzbQdcS 2qlJC9/YgIoJk2KOtWbPJYjNhLixP6Q5D9kCnusSTJV882sFqV4Wg8y4Z+LoE53MW4LTTLPtW//e 5XOsIzstAL81VXQJSdhJWBp/kjbmUZIO8yZ9HE0XvMnsQybQv0FfQKlERPSZ51eHnlAfV1SoPv10 Yy+xUGUJ5lhCLkMaTLTwJUdZ+gQek9QmRkpQgbLevni3/GcV4clXhB4PY9bpYrrWX1Uu6lzGKAgE JTm4Diup8kyXHAc/DVL17e8vgg8CAwEAAaOB9DCB8TAfBgNVHSMEGDAWgBStvZh6NLQm9/rEJlTv A73gJMtUGjAdBgNVHQ4EFgQUU3m/WqorSs9UgOHYm8Cd8rIDZsswDgYDVR0PAQH/BAQDAgGGMA8G A1UdEwEB/wQFMAMBAf8wEQYDVR0gBAowCDAGBgRVHSAAMEQGA1UdHwQ9MDswOaA3oDWGM2h0dHA6 Ly9jcmwudXNlcnRydXN0LmNvbS9BZGRUcnVzdEV4dGVybmFsQ0FSb290LmNybDA1BggrBgEFBQcB AQQpMCcwJQYIKwYBBQUHMAGGGWh0dHA6Ly9vY3NwLnVzZXJ0cnVzdC5jb20wDQYJKoZIhvcNAQEM BQADggEBAJNl9jeDlQ9ew4IcH9Z35zyKwKoJ8OkLJvHgwmp1ocd5yblSYMgpEg7wrQPWCcR23+Wm gZWnRtqCV6mVksW2jwMibDN3wXsyF24HzloUQToFJBv2FAY7qCUkDrvMKnXduXBBP3zQYzYhBx9G /2CkkeFnvN4ffhkUyWNnkepnB2u0j4vAbkN9w6GAbLIevFOFfdyQoaS8Le9Gclc1Bb+7RrtubTeZ tv8jkpHGbkD4jylW6l/VXxRTrPBPYer3IsynVgviuDQfJtl7GQVoP7o81DgGotPmjw7jtHFtQELF hLRAlSv0ZaBIefYdgWOWnU914Ph85I6p0fKtirOMxyHNwu8= -----END CERTIFICATE-----
- Now, it appears as if SSLLabs is caching the old result, because when I clear everything from Chrome on my Mac (from the "beginning of time"), the new certificate chain above is detected, as per my previous edit.
EDIT 3
The answer Michael Hampton gave was correct. However, the reason why the solution he proposed didn't work was because WHM has a bug with updating the certificate authority bundle. When this bug occurs, no matter what text you paste into the Certificate Authority Bundle field (on the SSL/TLS -> Install an SSL Certificate on a Domain page), the contents will be replaced with a different CA bundle despite WHM giving you a success message.