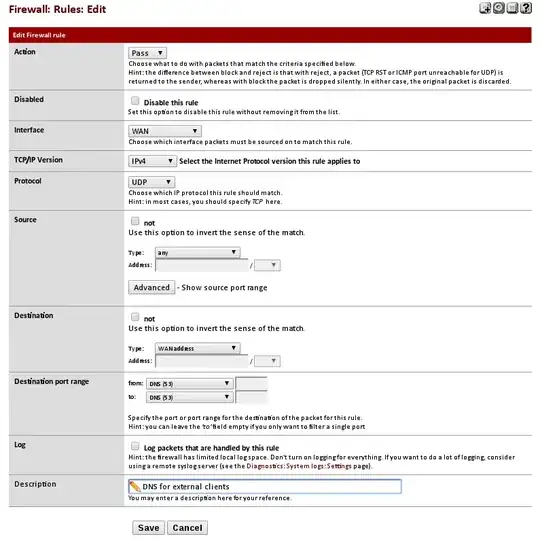
You don't want it allowing external DNS lookups. The built-in DNS Forwarder and Resolver are strictly for providing name resolution for your internal machines. If you want a public name server, use something that's designed to be a public name server. The BIND package if you must run it on the firewall, best to use a service provider or something on a separate server.
Your note on another comment that you switched to DNS Forwarder and opened it to the entire Internet means it's only a matter of hours likely until you're being used as part of a reflected DNS amplification DDoS attack, because you opened a recursive DNS resolver to the world. Take that rule off WAN so no one from the Internet can reach port 53. And you'd be better off switching back to Resolver, Unbound replies with "query refused" for good reason - its built-in ACL capabilities help ensure you're not able to make yourself open to flooding garbage traffic as part of a DDoS.