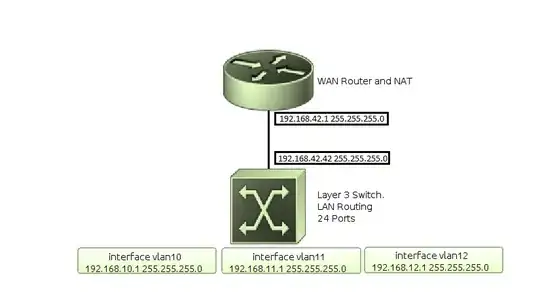
The network is pretty simple. Router-on-a-stick for nat/WAN access, Layer 3 switch for intervlan routing.
Router:
ip nat inside source list nated-nets interface FastEthernet0/0 overload
ip access-list extended nated-nets
permit ip 192.168.10.0 0.0.0.255 any
permit ip 192.168.11.0 0.0.0.255 any
permit ip 192.168.12.0 0.0.0.255 any
interface FastEthernet0/0
description [f0/0][ISP]
ip address dhcp
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
interface FastEthernet0/1.10
description [f0/1.10][vlan10]
encapsulation dot1Q 10
ip address 192.168.10.254 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat inside
ip virtual-reassembly in
interface FastEthernet0/1.11
description [f0/1.11][vlan11]
encapsulation dot1Q 11
ip address 192.168.11.254 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat inside
ip virtual-reassembly in
interface FastEthernet0/1.12
description [f0/1.12][vlan12]
encapsulation dot1Q 12
ip address 192.168.12.254 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip nat inside
ip virtual-reassembly in
Switch:
interface range gigabitEthernet 0/1-7
switchport mode access
switchport access vlan 10
spanning-tree portfast
switchport nonegotiate
interface range gigabitEthernet 0/8-14
switchport mode access
switchport access vlan 11
spanning-tree portfast
switchport nonegotiate
interface range gigabitEthernet 0/15-21
switchport mode access
switchport access vlan 12
spanning-tree portfast
switchport nonegotiate
interface GigabitEthernet0/24
description [g0/24][router]
switchport trunk encapsulation dot1q
switchport trunk allowed vlan 10-12
switchport mode trunk
switchport nonegotiate
load-interval 30
carrier-delay msec 0
spanning-tree portfast trunk
interface Vlan10
ip address 192.168.10.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip policy route-map vlan10
interface Vlan11
ip address 192.168.11.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip policy route-map vlan11
interface Vlan12
ip address 192.168.12.1 255.255.255.0
no ip redirects
no ip unreachables
no ip proxy-arp
ip policy route-map vlan12
route-map vlan10 permit 10
match ip address vlan-gateway
set ip next-hop 192.168.10.254
route-map vlan11 permit 10
match ip address vlan-gateway
set ip next-hop 192.168.11.254
route-map vlan12 permit 10
match ip address vlan-gateway
set ip next-hop 192.168.12.254
ip access-list extended vlan-gateway
deny ip 192.168.10.0 0.0.0.255 192.168.0.0 0.0.255.255
deny ip 192.168.11.0 0.0.0.255 192.168.0.0 0.0.255.255
deny ip 192.168.12.0 0.0.0.255 192.168.0.0 0.0.255.255
permit ip any any
Switch routing table:
Switch# show ip route
Gateway of last resort is not set
C 192.168.10.0/24 is directly connected, Vlan10
C 192.168.11.0/24 is directly connected, Vlan11
C 192.168.12.0/24 is directly connected, Vlan12
Desired outcome:
Source IP: 192.168.10.25
Destination IP: 192.168.11.15
Route: 192.168.10.25 --> 192.168.10.1 --> 192.168.11.15
Source IP: 192.168.10.25
Destination IP: 8.8.8.8
Route: 192.168.10.25 --> 192.168.10.1 --> 192.168.10.254 --> ISP
Things I'm trying to avoid:
Source IP: 192.168.10.25
Destination IP: 192.168.11.15
Route: 192.168.10.25 --> 192.168.10.1 --> 192.168.10.254 --> 192.168.11.15
Source IP: 192.168.10.25
Destination IP: 8.8.8.8
Route: 192.168.10.25 --> 192.168.10.1 --> 192.168.11.254 --> ISP
Although this configuration DOES work as is, it feels sloppy.
I'm also seeing unexpected results when viewing the access-lists. I have 12 terminal windows open pinging IPs in other local subnets and 5 pinging external subnets and I have a bunch of random youtube, vine, facebook, and other packet chatter rich websites open. I thought the number would be higher.
Extended IP access list vlan-gateway
10 deny ip 192.168.10.0 0.0.0.255 192.168.0.0 0.0.255.255
20 deny ip 192.168.11.0 0.0.0.255 192.168.0.0 0.0.255.255 (478 matches)
30 deny ip 192.168.12.0 0.0.0.255 192.168.0.0 0.0.255.255 (3062 matches)
40 permit ip any any (47 matches)