So I've been scratching my head around this problem for a few days now.
This is a quick schema of our infrastructure :
- Our Primary Domain Controller is running in an hypervisor, in our datacenter. There are two stacks of firewalls (Fortigate FG200D and pfSense) before running into our MPLS network.
- The new domain controller is running on a baremetal install, in one of our sites, connected to the MPLS and behind also two layers of firewalls (Fortigate FG100D and pfSense).
Both servers are running Windows 2012 R2 and they are both up to date. The existing domain controller will be called DC-AD and the new will be RNS.
I have also disabled both Windows Firewalls and made a allow all rule in our firewalls between the two DC (at least, DC (DC-AD) and i-would-like-to-be-DC (RNS) ).
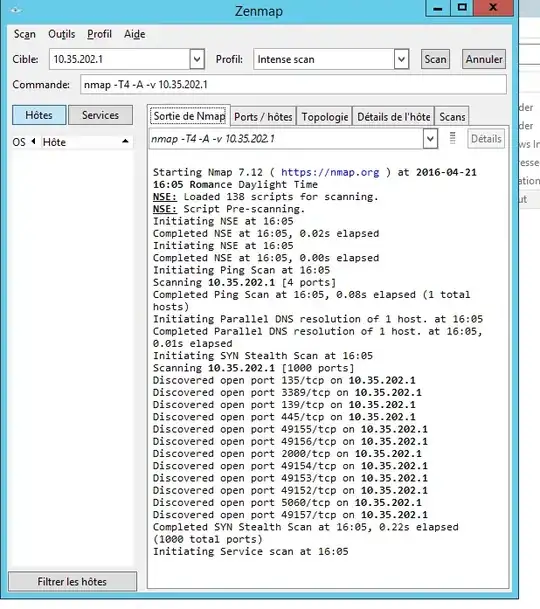
Here are the results of a nmap scan :
- From RNS towards DC-AD :
- From DC-A towards RNS :
I have tried everything I can think of or anything that I could find on the internet, but most of the problems are from blocked ports in the firewall.