My routing knowledge is a little rusty. I have a fibre internet connection hooked up like this:
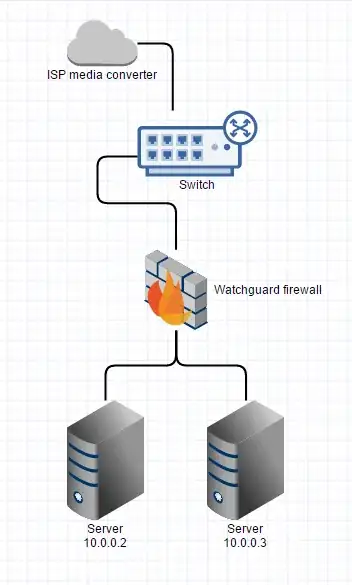
The managed switch breaks out VLANS for transparent lan service that is also through the ISP's box. I think that's mostly irrelevant for this problem, so I've left it out of the diagrams.
I have two /29 subnets (using example addresses from RFC5735):
- 192.0.2.144/29 (.144-151) - the main one. Our gateway is 192.0.2.145, and the firewall's main address is 192.0.2.146.
- 203.0.113.88/29 (.88-.95) - second subnet that has no gateway and is routed by the ISP to the first one (I think, this is the part where I get confused).
The firewall has all the usable IP addresses of both subnets added to it's WAN interface, and does NAT to various servers.
Now I want to add a separate network with it's own firewall, outside of our firewall, and it needs it's own public IP address, like this:
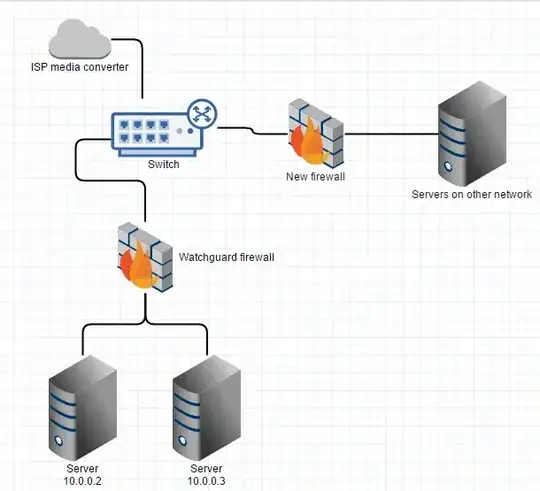
I am not using 203.0.113.94 yet, so I was going to remove it from the additional addresses on the existing firewall and give it to the new firewall...but that won't work will it? It has no gateway on its subnet.
Or I could rearrange things and give it one of the 192.0.2.144/29 addresses. Would that work properly and let both networks function properly? Is there a better way to do this?
I could attach the new firewall to the existing one if it could still get a real public IP, not NAT - but I don't know if there is any way to do that with the watchguard firewall. It would probably require further subnetting, and I'm almost out of IP addresses already.
The new network is to be our test lab (so I can finally stop testing things in production!). I don't want the two network to ever be able to speak to each other because it will have the same internal subnet and clones of production machines. I need the new firewall to have a public IP address, without any NAT.