I'm working on setting up a Squid 4.0 explicit proxy for group based AD authentication against a Active Directory domain (Server 2012 R2) with SSL bumping on a minimal CentOS 7 (64b) install.
The domain join was very sketchy using authconfig-tui but I managed to get it basically configured so AD users can authenticate via SSH, the Squid proxy works with authentication turned off. But kinit fails with:
[root@tc-icap squid]# kinit
kinit: Improper format of Kerberos configuration file while initializing Kerberos 5 library
After upping the debug logging for Squid and attempting to authenticate using a domain joined client, I see this in Squid's cache.log:
2016/03/02 11:12:56.151| Starting new negotiateauthenticator helpers...
2016/03/02 11:12:56.151| helperOpenServers: Starting 1/10 'negotiate_kerberos_auth' processes
2016/03/02 11:12:56| negotiate_kerberos_auth: ERROR: krb5_init_context: Improper format of Kerberos configuration file
2016/03/02 11:12:56| negotiate_kerberos_auth: ERROR: krb5_init_context: Improper format of Kerberos configuration file
2016/03/02 11:12:56.151| ERROR: Negotiate Authentication validating user. Result: {result=BH, notes={message: gss_acquire_cred() failed: An invalid name was supplied. Improper format of Kerberos configuration file; }}
2016/03/02 11:12:56.169| 11,5| HttpRequest.cc(473) detailError: current error details: 2/0
I really can't find what is wrong with my /etc/krb5.conf file. How should I proceed?
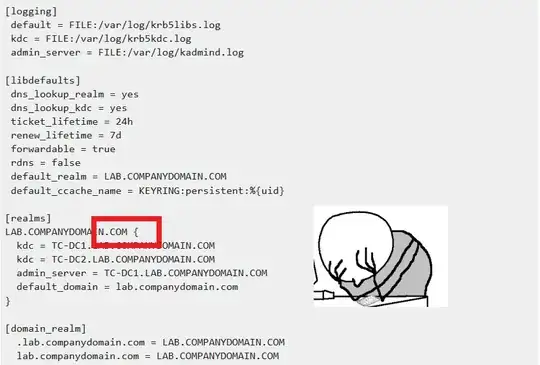
krb5.conf:
[logging]
default = FILE:/var/log/krb5libs.log
kdc = FILE:/var/log/krb5kdc.log
admin_server = FILE:/var/log/kadmind.log
[libdefaults]
dns_lookup_realm = yes
dns_lookup_kdc = yes
ticket_lifetime = 24h
renew_lifetime = 7d
forwardable = true
rdns = false
default_realm = LAB.COMPANYDOMAIN.COM
default_ccache_name = KEYRING:persistent:%{uid}
[realms]
LAB.COMPANYDOMAIN.COM {
kdc = TC-DC1.LAB.COMPANYDOMAIN.COM
kdc = TC-DC2.LAB.COMPANYDOMAIN.COM
admin_server = TC-DC1.LAB.COMPANYDOMAIN.COM
default_domain = lab.companydomain.com
}
[domain_realm]
.lab.companydomain.com = LAB.COMPANYDOMAIN.COM
lab.companydomain.com = LAB.COMPANYDOMAIN.COM
squid.conf:
# Squid 4 Explicit Proxy Configuration File
#
# Goals:
# 1. Install Minimal CentOS 7 VM to host Squid
# 2. Configure Squid for explicit proxying with the following features:
# a. ICAP (Content Adaptation) integration with CA Data Protection 15.0
# b. SSL Bumping (Peek and Splice -- Most recent and flexible configuration)
# c. Active Directory / LDAP Authentication and filtering rules
# d. User information pass-through to ICAP Agent (for mapping policy to authenticated users)
# e. Attempt content blocking / data in motion capture
# 3. Test functionality of intercepting Outlook Anywhere connectivity (without breaking clients.)
# 4. AD Group based access control and possibly blacklisting
# 5. Integration with Windows Certificate Authority services to generate certs/key requests
# 6. Kerberos / WINBIND authentication if AD/LDAP doesn't work. (kinit/keychain issues currently)
#
# Nice to haves:
# 1. ECAP (Encrypted ICAP support.) Squid has this, ICAP Agent does not.
# 2. Debug why ICAP URI's fail with DNS entries instead of IP address
# 3. Test fail open / closed configurations
# 4. Experiment with transparent proxying of traffic (avoid end user proxy configuration)
# 5. ICAP Content Adaptation Chain (Squeeze ClamAV in before or after DataProtection agent)
# 6. Automated auto-configuration deployment
# 7. Inject custom web X-Headers, check if headers are available as XML Data Lookups in Data Protection
#
# Reminder:
# 1. Check and reload configuration changes in Squid without restarting via:
# squid -k check
# squid -k reconfigure
# Debug logging: (very noisy!)
debug_options ALL,1 11,6
acl localnet src 0.0.0.1-0.255.255.255 # RFC 1122 "this" network (LAN)
acl localnet src 10.0.0.0/8 # RFC 1918 local private network (LAN)
acl localnet src 100.64.0.0/10 # RFC 6598 shared address space (CGN)
acl localhet src 169.254.0.0/16 # RFC 3927 link-local (directly plugged) machines
acl localnet src 172.16.0.0/12 # RFC 1918 local private network (LAN)
acl localnet src 192.168.0.0/16 # RFC 1918 local private network (LAN)
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl localnet src 25.0.0.0/8 # Hamachi local subnet (when installed)
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
# Enable Kerberos authentication, basic LDAP auth as fallback, block anonymous
auth_param negotiate program /usr/lib64/squid/negotiate_kerberos_auth -s HTTP/TC-ICAP.LAB.companydomain.com@LAB.COMPANYDOMAIN.COM #???
auth_param negotiate children 10 startup=0 idle=1
auth_param negotiate keep_alive off
auth_param basic program /usr/lib64/squid/basic_ldap_auth -R -b "dc=lab,dc=companydomain,dc=com" -D squidproxy@lab.companydomain.com -w Welcome1 -f (|userPrincipalName=%s)(sAMAccountName=%s)) -h tc-dc1.lab.companydomain.com
auth_param basic children 10
auth_param basic realm Internet Proxy
auth_param basic credentialsttl 1 minute
acl auth proxy_auth REQUIRED
# Recommended minimum Access Permission configuration:
http_access deny !Safe_ports
http_access deny CONNECT !SSL_ports
http_access allow localhost manager
http_access deny manager
http_access deny to_localhost
http_access deny !auth
http_access allow auth
http_access deny all
http_access allow localnet
http_access allow localhost
#
# Squid/DataProtection ACL's, ICAP Directives, Bumping cert directives
#
httpd_suppress_version_string on
sslcrtd_program /usr/lib64/squid/ssl_crtd -s /etc/squid/ssl_cert/ssl_db -M 12MB
sslcrtd_children 10
acl HTTP proto HTTP
always_direct allow all
#ssl_bump server-first all
ssl_bump stare all
ssl_bump bump all
sslproxy_cert_error allow all
sslproxy_cert_error allow all
icap_enable on
icap_send_client_ip on
icap_send_client_username on
icap_preview_enable off
icap_preview_size -1
icap_persistent_connections on
#icap_client_username_encode on
#icap_client_username_header X-Authenticated-User
# BK - Let us try using the IP address instead of DNS entries
icap_service sreq reqmod_precache icap://10.1.1.52:1344/reqmod
icap_service sresp respmod_precache icap://10.1.1.52:1344/respmod
adaptation_service_set aclreq sreq
adaptation_service_set aclresp sresp
adaptation_access aclreq allow all
adaptation_access aclresp allow all
# Deny requests that are not covered in above ACLs
http_access deny all
# The magic happens here:
# Directives: ssl-bump, generate dynamic certs, point to cert, path to sslcrtd??????
http_port 3128 ssl-bump generate-host-certificates=on dynamic_cert_mem_cache_size=12MB cert=/etc/squid/ssl_cert/myCA.pem
#http_port 3128 # This is the default
coredump_dir /var/spool/squid
# Note: Default refresh patterns below. Research these later for other protocols?
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
sssd.conf:
[sssd]
domains = LAB.companydomain.com
config_file_version = 2
services = nss, pam
[domain/LAB.companydomain.com]
ad_domain = LAB.companydomain.com
krb5_realm = LAB.COMPANYDOMAIN.COM
realmd_tags = manages-system joined-with-samba
cache_credentials = True
id_provider = ad
krb5_store_password_if_offline = True
default_shell = /bin/bash
ldap_id_mapping = True
use_fully_qualified_names = False
fallback_homedir = /home/%u@%d
access_provider = ad
realm list and net ads info:
[root@tc-icap squid]# net ads info
LDAP server: 10.1.1.20
LDAP server name: TC-DC1.LAB.companydomain.com
Realm: LAB.COMPANYDOMAIN.COM
Bind Path: dc=LAB,dc=COMPANYDOMAIN,dc=COM
LDAP port: 389
Server time: Wed, 02 Mar 2016 11:43:10 EST
KDC server: 10.1.1.20
Server time offset: 0
[root@tc-icap squid]# realm list
LAB.companydomain.com
type: kerberos
realm-name: LAB.COMPANYDOMAIN.COM
domain-name: lab.companydomain.com
configured: kerberos-member
server-software: active-directory
client-software: sssd
required-package: oddjob
required-package: oddjob-mkhomedir
required-package: sssd
required-package: adcli
required-package: samba-common
login-formats: %U
login-policy: allow-realm-logins
Edit: Here's a strace kinit to hopefully find a little more information about why Krb5 thinks that the file is invalid:
[root@tc-icap ~]# strace kinit
execve("/usr/bin/kinit", ["kinit"], [/* 25 vars */]) = 0
brk(0) = 0x7f9c4ee5d000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db29000
access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory)
open("/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=38289, ...}) = 0
mmap(NULL, 38289, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7f9c4db1f000
close(3) = 0
open("/lib64/libkadm5srv_mit.so.9", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\20o\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=121120, ...}) = 0
mmap(NULL, 2255200, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4d6e2000
mprotect(0x7f9c4d6fd000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4d8fd000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1b000) = 0x7f9c4d8fd000
mmap(0x7f9c4d8ff000, 39264, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f9c4d8ff000
close(3) = 0
open("/lib64/libkdb5.so.8", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0PF\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=79128, ...}) = 0
mmap(NULL, 2172848, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4d4cf000
mprotect(0x7f9c4d4e1000, 2093056, PROT_NONE) = 0
mmap(0x7f9c4d6e0000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x11000) = 0x7f9c4d6e0000
close(3) = 0
open("/lib64/libgssrpc.so.4", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0000[\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=134344, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db1e000
mmap(NULL, 2227080, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4d2af000
mprotect(0x7f9c4d2cd000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4d4cd000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1e000) = 0x7f9c4d4cd000
close(3) = 0
open("/lib64/libgssapi_krb5.so.2", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\20\300\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=316528, ...}) = 0
mmap(NULL, 2406656, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4d063000
mprotect(0x7f9c4d0ac000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4d2ac000, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x49000) = 0x7f9c4d2ac000
close(3) = 0
open("/lib64/libkrb5.so.3", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0PK\2\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=950496, ...}) = 0
mmap(NULL, 3033216, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4cd7e000
mprotect(0x7f9c4ce53000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4d053000, 65536, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0xd5000) = 0x7f9c4d053000
close(3) = 0
open("/lib64/libk5crypto.so.3", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0pG\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=202576, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db1d000
mmap(NULL, 2298360, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4cb4c000
mprotect(0x7f9c4cb7b000, 2093056, PROT_NONE) = 0
mmap(0x7f9c4cd7a000, 12288, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x2e000) = 0x7f9c4cd7a000
mmap(0x7f9c4cd7d000, 504, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f9c4cd7d000
close(3) = 0
open("/lib64/libcom_err.so.2", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0p\25\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=15840, ...}) = 0
mmap(NULL, 2109928, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4c948000
mprotect(0x7f9c4c94b000, 2093056, PROT_NONE) = 0
mmap(0x7f9c4cb4a000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x2000) = 0x7f9c4cb4a000
close(3) = 0
open("/lib64/libkrb5support.so.0", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\3406\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=62720, ...}) = 0
mmap(NULL, 2156136, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4c739000
mprotect(0x7f9c4c746000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4c946000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0xd000) = 0x7f9c4c946000
close(3) = 0
open("/lib64/libkeyutils.so.1", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\260\25\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=15688, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db1c000
mmap(NULL, 2109720, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4c535000
mprotect(0x7f9c4c538000, 2093056, PROT_NONE) = 0
mmap(0x7f9c4c737000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x2000) = 0x7f9c4c737000
close(3) = 0
open("/lib64/libresolv.so.2", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0@:\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=110808, ...}) = 0
mmap(NULL, 2202264, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4c31b000
mprotect(0x7f9c4c331000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4c531000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x16000) = 0x7f9c4c531000
mmap(0x7f9c4c533000, 6808, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f9c4c533000
close(3) = 0
open("/lib64/libselinux.so.1", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\240d\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=147120, ...}) = 0
mmap(NULL, 2246784, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4c0f6000
mprotect(0x7f9c4c117000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4c317000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x21000) = 0x7f9c4c317000
mmap(0x7f9c4c319000, 6272, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f9c4c319000
close(3) = 0
open("/lib64/libdl.so.2", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\320\16\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=19520, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db1b000
mmap(NULL, 2109744, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4bef2000
mprotect(0x7f9c4bef5000, 2093056, PROT_NONE) = 0
mmap(0x7f9c4c0f4000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x2000) = 0x7f9c4c0f4000
close(3) = 0
open("/lib64/libc.so.6", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0 \34\2\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=2107816, ...}) = 0
mmap(NULL, 3932736, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4bb31000
mprotect(0x7f9c4bce7000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4bee7000, 24576, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x1b6000) = 0x7f9c4bee7000
mmap(0x7f9c4beed000, 16960, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f9c4beed000
close(3) = 0
open("/lib64/libpthread.so.0", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\240l\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=142304, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db1a000
mmap(NULL, 2208864, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4b915000
mprotect(0x7f9c4b92b000, 2097152, PROT_NONE) = 0
mmap(0x7f9c4bb2b000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x16000) = 0x7f9c4bb2b000
mmap(0x7f9c4bb2d000, 13408, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_ANONYMOUS, -1, 0) = 0x7f9c4bb2d000
close(3) = 0
open("/lib64/libpcre.so.1", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\360\25\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=398272, ...}) = 0
mmap(NULL, 2490888, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4b6b4000
mprotect(0x7f9c4b714000, 2093056, PROT_NONE) = 0
mmap(0x7f9c4b913000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x5f000) = 0x7f9c4b913000
close(3) = 0
open("/lib64/liblzma.so.5", O_RDONLY|O_CLOEXEC) = 3
read(3, "\177ELF\2\1\1\0\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0000/\0\0\0\0\0\0"..., 832) = 832
fstat(3, {st_mode=S_IFREG|0755, st_size=153192, ...}) = 0
mmap(NULL, 2245240, PROT_READ|PROT_EXEC, MAP_PRIVATE|MAP_DENYWRITE, 3, 0) = 0x7f9c4b48f000
mprotect(0x7f9c4b4b3000, 2093056, PROT_NONE) = 0
mmap(0x7f9c4b6b2000, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_FIXED|MAP_DENYWRITE, 3, 0x23000) = 0x7f9c4b6b2000
close(3) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db19000
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db18000
mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db16000
arch_prctl(ARCH_SET_FS, 0x7f9c4db16840) = 0
mprotect(0x7f9c4bee7000, 16384, PROT_READ) = 0
mprotect(0x7f9c4bb2b000, 4096, PROT_READ) = 0
mprotect(0x7f9c4b6b2000, 4096, PROT_READ) = 0
mprotect(0x7f9c4b913000, 4096, PROT_READ) = 0
mprotect(0x7f9c4c0f4000, 4096, PROT_READ) = 0
mprotect(0x7f9c4c317000, 4096, PROT_READ) = 0
mprotect(0x7f9c4c531000, 4096, PROT_READ) = 0
mprotect(0x7f9c4c737000, 4096, PROT_READ) = 0
mprotect(0x7f9c4c946000, 4096, PROT_READ) = 0
mprotect(0x7f9c4cb4a000, 4096, PROT_READ) = 0
mprotect(0x7f9c4cd7a000, 8192, PROT_READ) = 0
mprotect(0x7f9c4d053000, 53248, PROT_READ) = 0
mprotect(0x7f9c4d2ac000, 4096, PROT_READ) = 0
mprotect(0x7f9c4d4cd000, 4096, PROT_READ) = 0
mprotect(0x7f9c4d6e0000, 4096, PROT_READ) = 0
mprotect(0x7f9c4d8fd000, 4096, PROT_READ) = 0
mprotect(0x7f9c4dd32000, 4096, PROT_READ) = 0
mprotect(0x7f9c4db2a000, 4096, PROT_READ) = 0
munmap(0x7f9c4db1f000, 38289) = 0
set_tid_address(0x7f9c4db16b10) = 1173
set_robust_list(0x7f9c4db16b20, 24) = 0
rt_sigaction(SIGRTMIN, {0x7f9c4b91b780, [], SA_RESTORER|SA_SIGINFO, 0x7f9c4b924100}, NULL, 8) = 0
rt_sigaction(SIGRT_1, {0x7f9c4b91b810, [], SA_RESTORER|SA_RESTART|SA_SIGINFO, 0x7f9c4b924100}, NULL, 8) = 0
rt_sigprocmask(SIG_UNBLOCK, [RTMIN RT_1], NULL, 8) = 0
getrlimit(RLIMIT_STACK, {rlim_cur=8192*1024, rlim_max=RLIM64_INFINITY}) = 0
statfs("/sys/fs/selinux", 0x7ffedf4d6310) = -1 ENOENT (No such file or directory)
statfs("/selinux", 0x7ffedf4d6310) = -1 ENOENT (No such file or directory)
brk(0) = 0x7f9c4ee5d000
brk(0x7f9c4ee7e000) = 0x7f9c4ee7e000
open("/proc/filesystems", O_RDONLY) = 3
fstat(3, {st_mode=S_IFREG|0444, st_size=0, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db28000
read(3, "nodev\tsysfs\nnodev\trootfs\nnodev\tb"..., 1024) = 276
stat("/etc/sysconfig/64bit_strstr_via_64bit_strstr_sse2_unaligned", 0x7ffedf4d61f0) = -1 ENOENT (No such file or directory)
read(3, "", 1024) = 0
close(3) = 0
munmap(0x7f9c4db28000, 4096) = 0
open("/usr/lib/locale/locale-archive", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=106065056, ...}) = 0
mmap(NULL, 106065056, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7f9c44f68000
close(3) = 0
ioctl(0, SNDCTL_TMR_TIMEBASE or SNDRV_TIMER_IOCTL_NEXT_DEVICE or TCGETS, {B38400 opost isig icanon echo ...}) = 0
ioctl(1, SNDCTL_TMR_TIMEBASE or SNDRV_TIMER_IOCTL_NEXT_DEVICE or TCGETS, {B38400 opost isig icanon echo ...}) = 0
ioctl(2, SNDCTL_TMR_TIMEBASE or SNDRV_TIMER_IOCTL_NEXT_DEVICE or TCGETS, {B38400 opost isig icanon echo ...}) = 0
futex(0x7f9c4c947510, FUTEX_WAKE_PRIVATE, 2147483647) = 0
futex(0x7f9c4c9473b0, FUTEX_WAKE_PRIVATE, 2147483647) = 0
futex(0x7f9c4d061420, FUTEX_WAKE_PRIVATE, 2147483647) = 0
futex(0x7f9c4d062550, FUTEX_WAKE_PRIVATE, 2147483647) = 0
stat("/etc/krb5.conf", {st_mode=S_IFREG|0644, st_size=1003, ...}) = 0
open("/etc/krb5.conf", O_RDONLY) = 3
fcntl(3, F_SETFD, FD_CLOEXEC) = 0
fstat(3, {st_mode=S_IFREG|0644, st_size=1003, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db28000
read(3, "[logging]\n default = FILE:/var/l"..., 4096) = 1003
close(3) = 0
munmap(0x7f9c4db28000, 4096) = 0
open("/usr/share/locale/locale.alias", O_RDONLY|O_CLOEXEC) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=2502, ...}) = 0
mmap(NULL, 4096, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f9c4db28000
read(3, "# Locale name alias data base.\n#"..., 4096) = 2502
read(3, "", 4096) = 0
close(3) = 0
munmap(0x7f9c4db28000, 4096) = 0
open("/usr/share/locale/en_US.UTF-8/LC_MESSAGES/mit-krb5.mo", O_RDONLY) = -1 ENOENT (No such file or directory)
open("/usr/share/locale/en_US.utf8/LC_MESSAGES/mit-krb5.mo", O_RDONLY) = -1 ENOENT (No such file or directory)
open("/usr/share/locale/en_US/LC_MESSAGES/mit-krb5.mo", O_RDONLY) = 3
fstat(3, {st_mode=S_IFREG|0644, st_size=410, ...}) = 0
mmap(NULL, 410, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7f9c4db28000
close(3) = 0
open("/usr/share/locale/en.UTF-8/LC_MESSAGES/mit-krb5.mo", O_RDONLY) = -1 ENOENT (No such file or directory)
open("/usr/share/locale/en.utf8/LC_MESSAGES/mit-krb5.mo", O_RDONLY) = -1 ENOENT (No such file or directory)
open("/usr/share/locale/en/LC_MESSAGES/mit-krb5.mo", O_RDONLY) = -1 ENOENT (No such file or directory)
write(2, "kinit: Improper format of Kerber"..., 54kinit: Improper format of Kerberos configuration file ) = 54
write(2, "while initializing Kerberos 5 li"..., 37while initializing Kerberos 5 library) = 37
write(2, "\n", 1
) = 1
exit_group(1) = ?
+++ exited with 1 +++