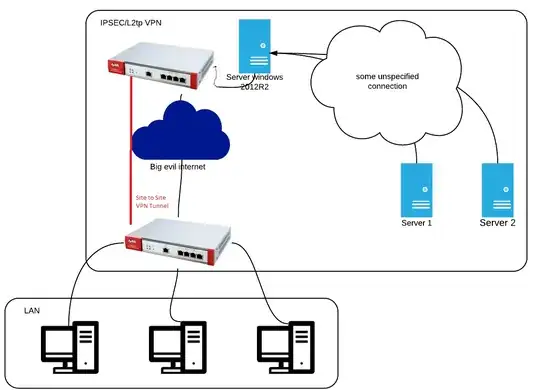
I recommand a zywall at both end if you can. (Your question is almost a duplicate of that one by the way)
For your question please see there for a guide, and some link. (zywall is not wrote).
To see some example to configure the zywall to other type network gear to make a site to site vpn, there is some resources (there and there).
With both links I gave you can see a zywall <==> cisco tunnel, and a microsoft <==> cisco tunnel's example, so it should give you an actual idea of what to do. (As zywall did not wrote that KB for a zywall <==> microsoft tunnel)
Introduction
Microsoft® Windows® Server 2012 R2 industry standard IKEv2 tunnel for
VPN connectivity (both point-to-site and site-to-site). This enables
customers with existing third party VPN devices to easily deploy the
Windows Server 2012 R2 VPN gateway and interoperate with these devices
to perform branch-site networking.
This document covers the working configurations for some of the
popular third party VPN devices that can be deployed to work with
Windows Server 2012 R2 VPN. The configuration for a Windows gateway is
also included to server as a guideline for an interoperable deployment
with the third party devices. Windows Server Gateway
Windows Server 2012 R2 gateway can be configured for point-to-site
(P2S) VPN, site-to-site (S2S) VPN, dynamic BGP Routing or a
combination of these features. The P2S VPN support and its
interoperability on the Windows Server 2012 R2 remains unchanged and
the details are available here. The dynamic BGP Routing support is the
implementation of standard BGP4 protocol. This enables the dynamic BGP
routing to be configured between the Windows gateway and the secondary
branch site (provided the site is using a Windows or a third party
BGP4 router).
> To establish a S2S VPN connection between a multi-tenant Windows
Server 2012 R2 VPN gateway and your third party device, you will have
to make sure the third party device supports IKEv2 tunnelling protocol
and that the IPSec parameter configuration is compatible to that of
the Windows configuration. IPSec Configuration
This section lists the various IPSec configuration parameters for
IKEv2 tunnel available on the Windows Server 2012 R2 S2S VPN Gateway.
Configuration via SC-VMM
Configuration via SC-VMM offers even more customizable IPSec
configuration options like can be seen in this VM Network Properties
window (SC-VMM > VM and Service > VM Networks > Tenant Network >
Properties)
Figure 1: SC-VMM VPN connection configuration
We have validated a set of standard third party S2S VPN devices in for
interoperability with Windows Server 2012 R2 VPN gateway. These
compatible devices are listed below along with the example
configuration for these device families to help configure your VPN
device.
If you don’t see your device in the known compatible VPN device list
and want to use the device for your VPN connection, you’ll need to
verify that it meets the minimum requirements outlined in the previous
section. Devices meeting the minimum requirements should also work
well with Windows Server 2012 R2 Gateway.
Vendor
Device Family
OS Version
Example configuration
CheckPoint
Security Gateway
R75.40
R75.40VS
Configuration instructions
Cisco
ASA 5500 series
ASA v9.0 (3)
Device Manager v 7.1(2)
[View:~/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-55-08/Cisco-ASA-5510-config.txt:50:50]
Cisco
ASR
IOS 15.2
Cisco ASR templates
Cisco
ISR
IOS 15.1
Cisco ISR templates
Fortinet
FortiGate
FortiOS 5.0.7
Configuration instructions
Juniper
SRX series
JunOS 11.4
Juniper SRX templates
Juniper
SRX series
JunOS 12.1
[View:~/cfs-file.ashx/__key/communityserver-blogs-components-weblogfiles/00-00-00-55-08/Juniper-SRX100-config.txt:50:0]
Juniper
J-Series
JunOS 11.4
Juniper J-series templates
Juniper
ISG
ScreenOS 6.3
Juniper ISG templates
Juniper
SSG
ScreenOS 6.2
Juniper SSG templates
If you opt for a zywall at both end, there how I see it, and the official guide to do it by zywall there.