I recently had a problem where a remote service requesting the IP address for my server (with a hosted DNS provider) was responding with:
DNS problem: SERVFAIL looking up A for mysql.xavamedia.nl
(Update: the remote service mentioned here is Let's Encrypt; I filed a bug against their issue tracker, which led me on this path.)
In testing on my local network, I was able to see that I sometimes get an empty DNS response from the hosted DNS server. Apparently this is intermittent because it happens only when the DNS records are not in the cache, and it's only a problem when the DNS server is really busy.
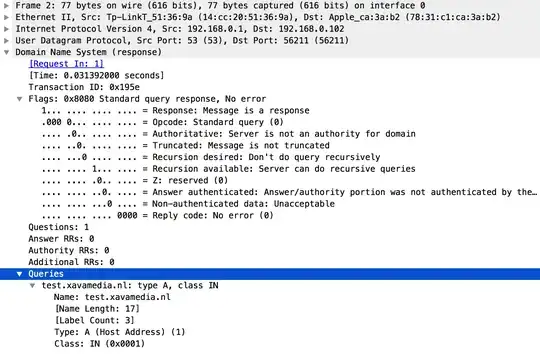
Here's a Wireshark description of an empty response message:
Of course, since most DNS queries and responses are sent over UDP, a local resolver will just wait a while for the response, and then give up. What I am now left wondering is, are there guidelines for DNS response times? My DNS hoster sort of shrugged and said that my local resolver sent the empty response too soon. I've never had this problem before, but I'm surprised at the failure mode -- an empty DNS response without an error code.
Does someone know of some guidelines on how this is supposed to work, and when/how I can prove my DNS hosting is doing something wrong?