We are migrating from one set of addresses to another set, both /24, and trying to minimize any down time during the migration. Ideally we'd run both for a period of time as we shut down the old circuits. There are a total of 4 internet connections, with each pair running BGP.
Each of these is then routed to a Cisco ASA, which is connected to a switch which has multiple servers connected on that subnet.
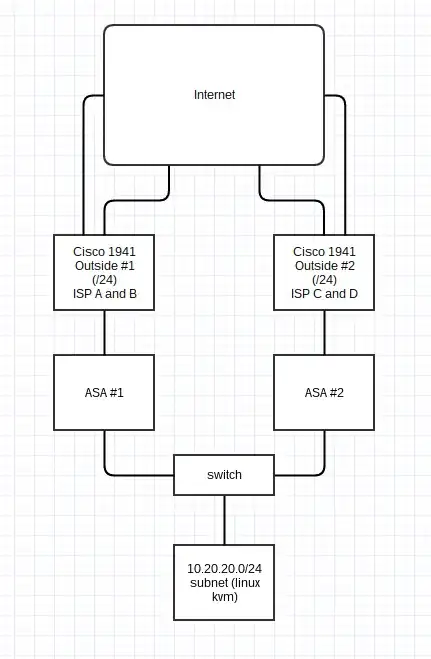
In the above diagram, the left hand portion is what exists today, and I'm looking to add the right side.
I've connected the ASA and have both of them on the 10.20.20.0/24 subnet, with the first ASA interface as 10.20.20.1 and the second ASA interface as 10.20.20.254.
The issue here is that all of the servers have 10.20.20.1 as their default route, and I'd really like to route traffic back the way it came in. That is, internet -> ASA #2 -> server -> back to ASA #2. As it is today, of course, it sends the response back to ASA #1 and it doesn't find a translation for it.
Am I going about this the wrong way?
Edit: I should mention that Outside #1 and Outside #2 have different public /24 networks. We're migrating from an ISP provided block to our own block.