I have been struggling trying to figure out the right way to do this.
Here is my setup. I have 2 sangoma servers (Lync 2013 in a box) The Front End server is is the main server. The Reverse Proxy and Edge Servers are VMs on the Front End.
LyncFE1 I go through the Deployment Wizard and I see I have 2 internal interfaces that have internal CA Certs. All good. Then I have one external interface with the godaddy cert. 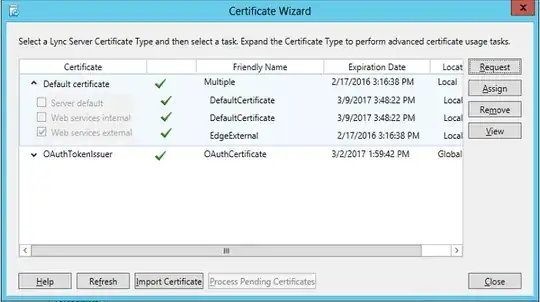
Edge1 I go through the Deployment wizard I have one internal and one external interface each with the appropriate certs.
Reverse Proxy 1 I use IIS and it has the right Cert.
Then I go to
LyncFE2 and all 3 interfaces I have the internal Cert.
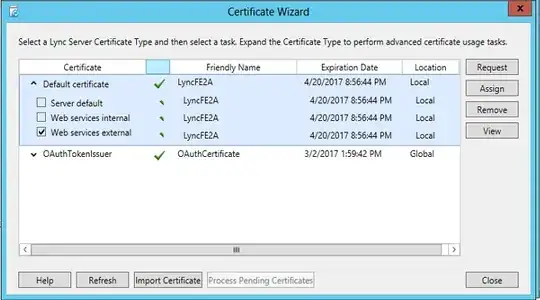
I had a vendor who installed this and we are ironing out the issues but they are gone and I need to renew the godaddy. I have followed the steps of building a request (Checking all private keys to be exportable) and pasting it on godaddy's site and getting the IIS version of the certs. But when I go import the cert I does not show up in the assignable cert. So I tried going through certmagr and It installs again it is not available to assign and If I try to export it I do not get the option to export the Private keys.
I built the request on the FE and installed on the FE. Should I be building the request on the Edge? Should I be downloading a different version like exchange? What am I doing wrong? Shouldn't LyncFE2 have the godaddy cert?