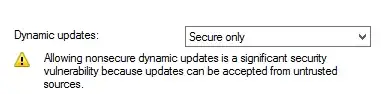
What are the practical risks of enabling the unsecure DNS updates on Windows?
As far as I found enabling the unsecure DNS updates is a requirement for enabling DHCP Linux clients from registering their names with a FQDN.
I do want to know that are the practical risks involved in this in order to evaluate if that's ok to have these enabled or not.
As far as I know a machine would not be able to takeover another reserved name which would be the only real concern that I now.
Obviously it would be the DDOS but considering that we are talking about intranet here, I doubt this could be a real risk.
Do you have it enable on your domain or not? Did you ever had to disable it due to having some problems with it?