Context:
I have a Dedicated Server hosted on Digital Ocean, called as "Droplet" and then, on it i have installed CentOS 6, and my mailing server is using EXIM.
Problem:
I am having spam issues on my server, i am being blacklisted and Digital Ocean is blocking my SMTP due to pishing, so i need to find where is the source of the spam to close the security breach or delete the potencial spam or somewhat else.
Something that i've tried:
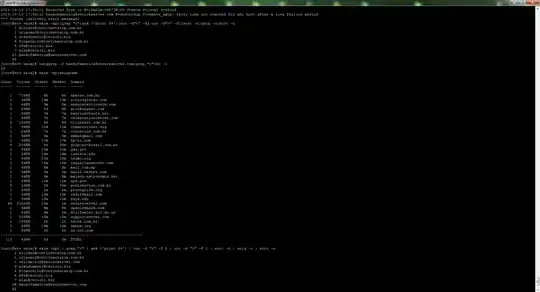
Here on the image, as you can see i found the emails that are the spam problem in my exim mail server, by the way i dont know how to see where is the source of that email, i can access the spam mail header and i know from what recipient and to what recpient that the email is going, as far i know the header.
The thing is that im a little new on that and i dont know how to identify and close the problem, any hints for that??
Important:
I do not want to know what i need to do, because i already know that. The thing is that i want to know how to do that.