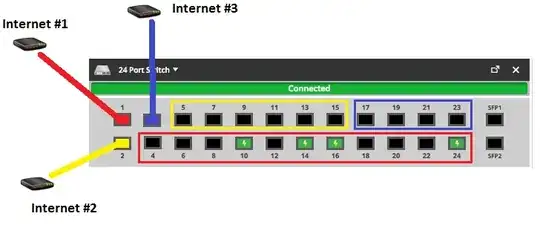
I'm trying to plan for the following Small Office network setup:
- 3x Internet connections
- Things connected to the port in each colour can only get routed through their corresponding internet port.
for example:
Internet 1 (RED) - ports 4, 6, 8, 10 ... 22, 24 only go out via port 1.
I don't care if a device from the RED ports can see a device from another colour.
Is this called VLan segmenting? Do I need to tag each port a VLAN ID?
Yes, I'm new to this so please be kind. Of course, I've got the wrong terminology so I would also be grateful for any help in getting corrected on the terminology used, here.
Further notes: - I'm only using one switch. not two or more than need to joined. - 3x internet connections because it's cheaper in AU to get 3x ADSL connections that 1x 'fast office' internet (like 40/10 or 100/10, etc)... - Each internet connection is doing something unique (eg. voip vs internet vs multimedia)
UPDATE 1:
Also, I'm assuming each colour would have it's own IP range? eg.
- RED : 192.168.0.1/24
- YELLOW: 192.168.1.1/24
- BLUE: 192.168.2.1/24
(and the modem/routers are acting as the DHCP servers for those coloured ports).
UPDATE 2: Switch is a brand spankin' new Ubiquiti Unfi 24port Switch.