Problem: Our mobile app can no longer establish a secure connection to our web-service since iOS 9 now uses ATS.
Background: iOS 9 introduces App Transport Security
Server Setup: Windows Server 2008 R2 SP1 (VM) IIS 7.5, SSL certs from digicert. Windows firewall off.
Key RSA 2048 bits (e 65537)
Issuer DigiCert SHA2 Secure Server CA
Signature algorithm SHA512withRSA
These are the App Transport Security requirements:
The server must support at least Transport Layer Security (TLS) protocol version 1.2. Connection ciphers are limited to those that provide forward secrecy (see the list of ciphers below.) Certificates must be signed using a SHA256 or better signature hash algorithm, with either a 2048 bit or greater RSA key or a 256 bit or greater Elliptic-Curve (ECC) key. Invalid certificates result in a hard failure and no connection. These are the accepted ciphers:
TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA384 TLS_ECDHE_ECDSA_WITH_AES_256_CBC_SHA TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_ECDSA_WITH_AES_128_CBC_SHA TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA
What has been tried:
- Adding exceptions in the mobile app to allow our domain works, but I do not want to go with this unsecured method, I want to fix our SSL.
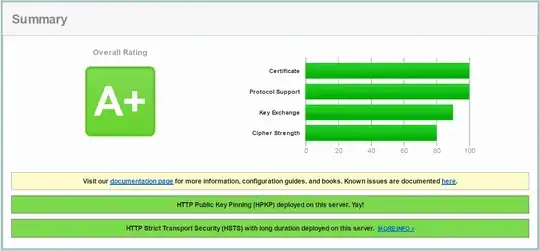
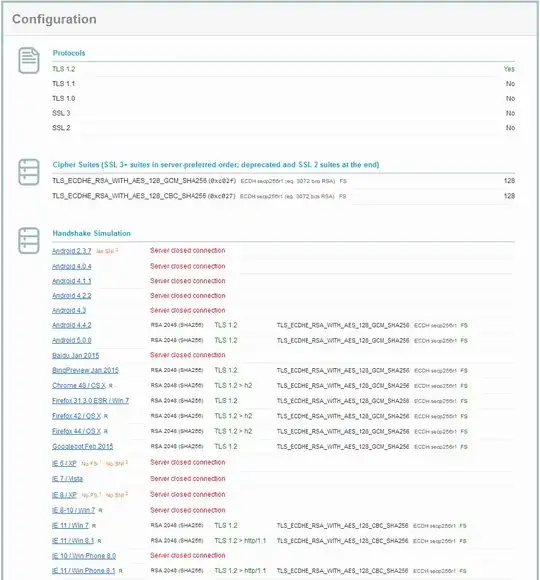
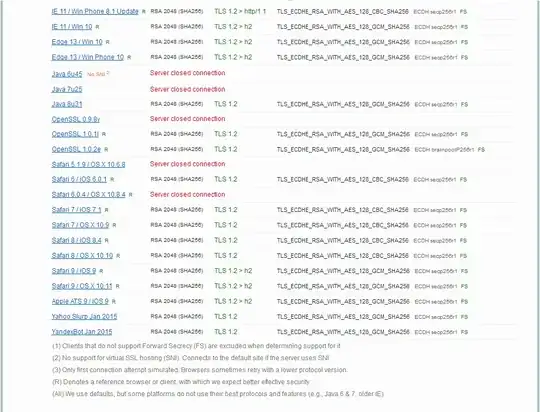
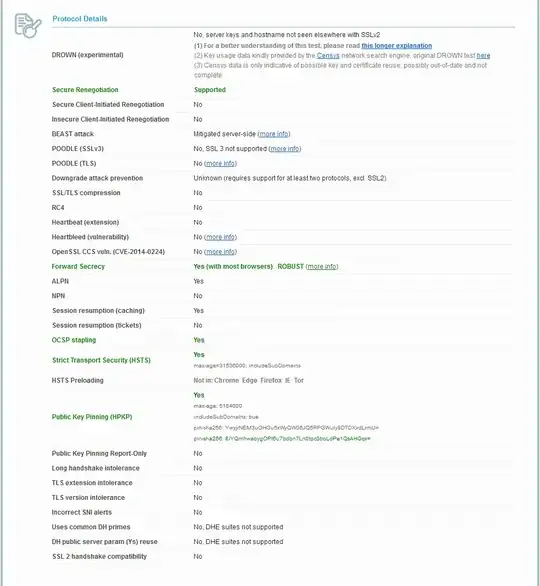
- Used IIS Crypto to use 'best practice', tried 'pci', and custom setups. Even tried modifying the crypto suite to just the list above, and reordering. After each attempt, server is rebooted, and and SSL Labs was ran (after clearing cache). I was successful at going from a F rating to an A, and even A-, but this only resulted in iOS 8 and 9 being unable to establish secure connections. (NSURLErrorDomain Code=-1200 and _kCFStreamErrorCodeKey=-9806)
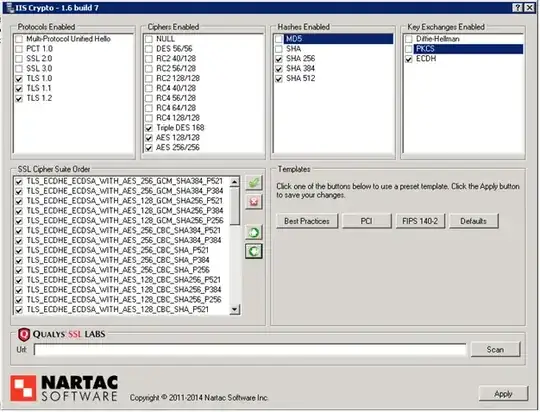
- Restored VM and tried a powershell script Setup your IIS for SSL Perfect Forward Secrecy and TLS 1.2 I even made a second attempt where I edited out cyphers from the power script to a minimal list of what is required.
Results: Always similar, ratings of A or A-. iOS8 and iOS9 can't negotiate secure connection. Handshake Simulation results in "Protocol or cipher suite mismatch" for Safari and iOS products.
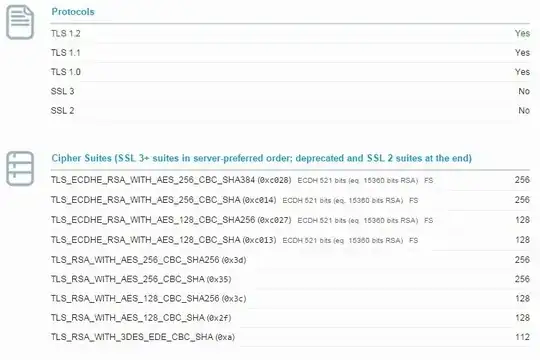
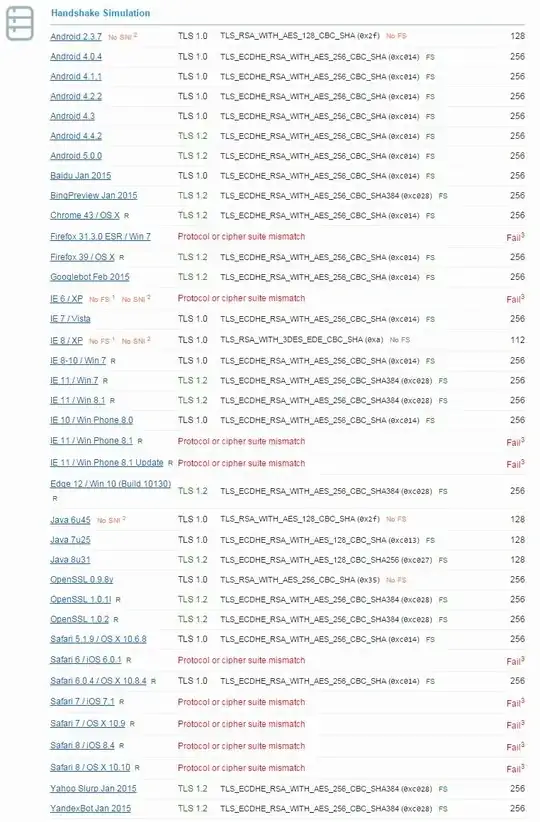
UPDATE After working with Apple support, we did some packet trace capture:
$ tcpdump -n -r trace.pcap
reading from file trace.pcap, link-type EN10MB (Ethernet)
client > server [S], seq 1750839998, win 65535, length 0
server > client [S.], seq 2461151276, ack 1750839999, win 8192, length 0
client > server [.], ack 1, win 4104, length 0
client > server [P.], seq 1:175, ack 1, win 4104, length 174
server > client [R.], seq 1, ack 175, win 0, length 0
The first three packets are the classic SYN - SYN-ACK - ACK three way handshake that sets up the TCP connection. The fourth packet is iOS sending your server a TLS Client Hello message, the first step in setting up a TLS connection over that TCP connection. I’ve pulled apart this message and it looks reasonable enough. In the fifth packet the server simply drops the connection (by sending a RST).
Does anyone know why IIS 7.5 would be doing a RST?