I've been managing the NPS Server for a while and thought it was time to treat it a valid SSL certificate.
The setup
I bought a wildcard SSL certificate from comodo, compiled it to an .pfx certificate (including the comodo chain) and installed it on the Server. The pfx file is fine since I installed it on IIS7 and it gets validated in every browser.
I then chose the certificate in the NPS like this (sorry it's german but should be the same for the english version):
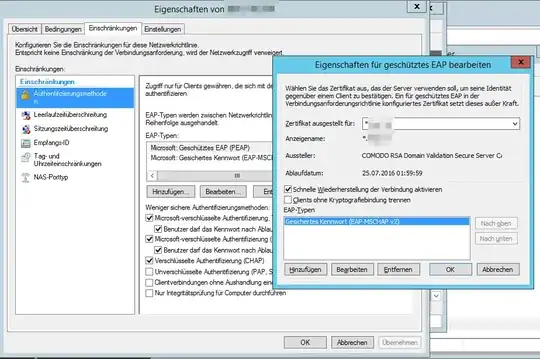
The problem
Now when a client connects to the wifi network they'll get a message like "authorization failed" or on windows it'll just re-open the authentication dialogue in a loop. Iphones will tell the client directly that they can't verify the certificate and give them the choice to ignore it.
The server log then says that the user account can't be found which is not the case but when I disable certificate check on a client, it connects just fine.
This means the certificate is not valid to the client.
What I think happens
- The certificate is a wildcard for the domain *.example.com, the Active directory domain is location1.example.com. Might there be a delegation problem?
- If I import the certificate to my AD cert server, can I create a sub-certificate for radius.location1.example.com?
Is there anything else I'm missing or are wildcard certificates just not useable with radius on Windows Server?
I'm thankful for any pointers