I have an AD FS claims provider set up and a Shibboleth SP successfully authenticating against it.
I am attempting to have the Active Directory attributes sent to the SP.
I followed this article to attempt to send the claims: https://technet.microsoft.com/en-us/library/gg317734(v=ws.10).aspx
The relevant section is Step 2: Configure AD FS 2.0 as the Identity Provider and Shibboleth as the Relying Party --> Configure AD FS 2.0 --> Edit Claim Rules for Relying Party Trust --> To configure eduPerson claims for sending to a relying party trust:
In Step 16, it states that I should paste or type the following (and has it in 2 code blocks):
c:[Type == "http://schemas.xmlsoap.org/claims/Group", Value == "Domain Users"]
and
=> issue(Type = "urn:oid:1.3.6.1.4.1.5923.1.1.1.9", Value = "member@contoso.com", Properties["http://schemas.xmlsoap.org/ws/2005/05/identity/claimproperties/attributename"] = "urn:oasis:names:tc:SAML:2.0:attrname-format:uri");
I believe that it was meant to be a single statement (please correct me if I'm wrong) so my entry is as follows:
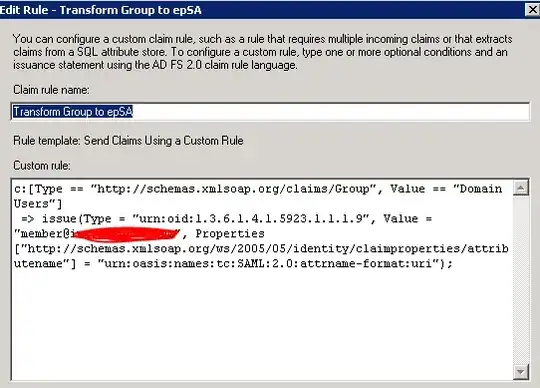
I am testing with the givenName, so I added the following:
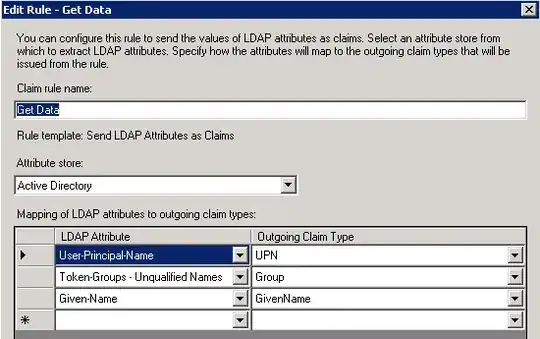
On the Shibboleth SP machine, I edited the attribute-map.xml by adding the following and then I restarted the Shibboleth service:
<Attribute name="urn:mace:dir:attribute-def:GivenName" id="GivenName"/>
When I browsed to the website and re-authenticated with AD FS, I am not seeing the givenName showing. I have an index file that outputs all of the headers and their values.
Edit: Solution to my issue
I got the UPN to send as the epPN. The above rules (the rules in the article) worked, but I had to edit the attribute-policy.xml on the Shibboleth SP to disable the scoping rules, since I didn't have that part set up properly.
I commented out the following lines in the attribute-policy.xml
afp:AttributeRule attributeID="eppn">
<afp:PermitValueRuleReference ref="ScopingRules"/>
</afp:AttributeRule>