I have CISCO 2921 and Sonicwall NSA 3600. I am trying to setup Site to site VPN. I am getting:
Received notify. NO_PROPOSAL_CHOSEN
in Sonicwall logs and the VPN is not setup.
It looks like the phase 1 is OK as I am getting:
Info VPN IKE IKE Initiator: Start Quick Mode (Phase 2). SONIC_WALL_IP, 500 CISCO_IP, 500 VPN Policy: test
in the sonicwall logs just before NO_PROPOSAL_CHOSEN message.
I have checked:
- Authentication/Authorization algorithms on both side and they match(DES/SHA1)
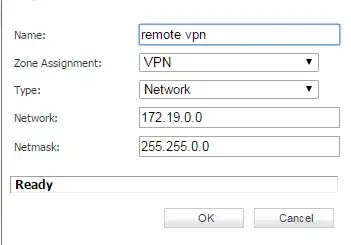
- Correct subnets are configured on both side of the connection(172.16.0.0 on Sonicwall side and 172.19.0.0 on Cisco side)
Both debug crypto isakmp and debug crypto ipsec on cisco doesn't give me any output.
Because WAN interface is setup as /28 there is a a bit of nat-ing set up but I think it is not relevant so I removed it from the below CISCO config example, I will add it when requested. Computers connected to 172.19.0.0 have internet access with a correct IP address so I think that nat-ing is irrelevant.
Can someone please help me with this?I might be missing some configuration or I have made a stupid mistake.
Relevant cisco config:
// Phase 1
crypto isakmp policy 1
authentication pre-share
group 2
lifetime 28800
crypto isakmp key SECRET address SONICWALL_IP
//Phase 2
crypto ipsec security-association lifetime seconds 28800
crypto ipsec transform-set MYSET esp-des esp-sha-hmac
crypto map MYMAP 1 ipsec-isakmp
set peer SONICWALL_IP
set transform-set MYSET
match address 166
// WAN interface
interface GigabitEthernet0/0
description WAN
ip address CISCO_PUBLIC_IP 255.255.255.240
ip nat outside
ip virtual-reassembly in
duplex auto
speed auto
crypto map MYMAP
//LAN interface
interface GigabitEthernet0/1/3
switchport access vlan 72
no ip address
interface Vlan72
ip address 172.19.0.1 255.255.0.0
ip nat inside
ip virtual-reassembly in
access-list 166 permit ip 172.19.0.0 0.0.255.255 172.16.0.0 0.0.255.255
Sonicwallis setup as:
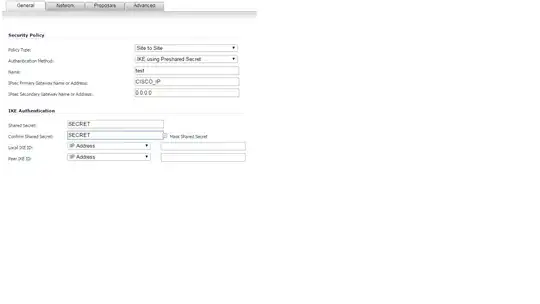
and the Network tab -> Remote Networks -> Choose destination network from list is set up as: