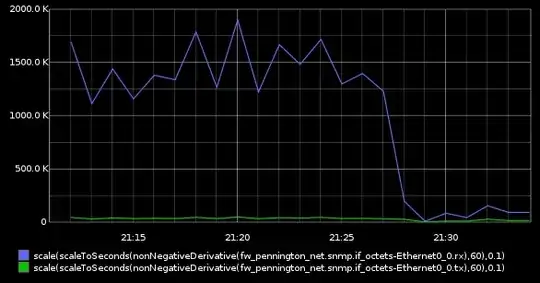
I am looking for a PCI or PCI Express based Network card with builtin VPN possibilities or a network card which allows to flash its firmware vyatta, ipcop , routeros or any similar os.
The idea is to allow remote support of a server system (access to its oob interface and os) even though the systems operating system is unable to boot correctly and setup the VPN connection by itself.
May this little drawing helps explaining it:
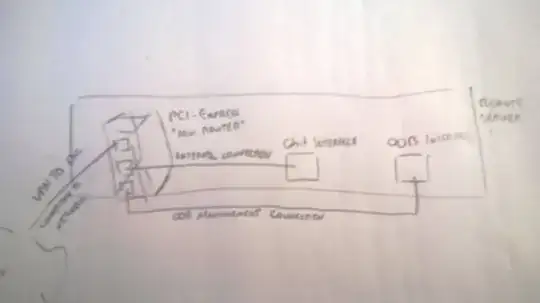
Do you know if such cards exist? Do you have experience with such a setup?