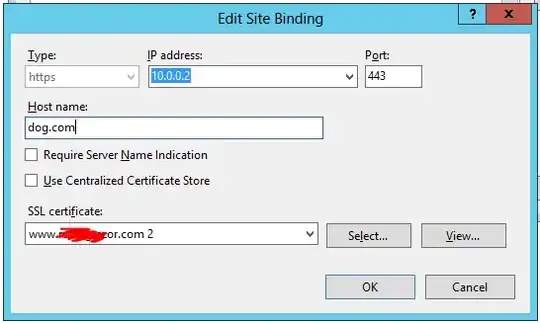
I have two different 'families' of related sites, each with their own UCC certificate on the same server.
I'm hosting them on the same IIS server, using one IP address for each family.
Both UCC certficates are from GoDaddy.
Every one of the bindings (for each SAN in the UCC) has 'Require Server Name indication' disabled.
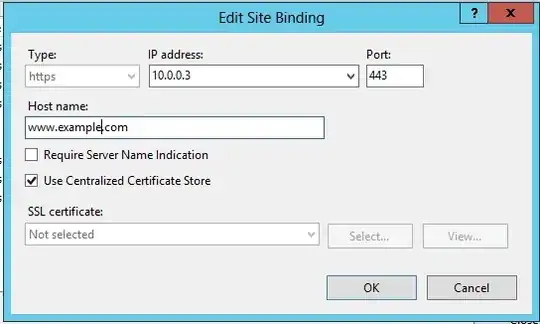
However when I try to hit the site from IE 8 on Windows XP only one of the 'families' of sites works. The other just doesn't negotiate.
When analyzing the SSL on SSLLabs.com I get the following result - telling me 'This site works only in browsers with SNI support.'
But how is this possible! I have disabled 'Require SNI' for every :443 binding.
I've even looked at the applicationHost.config file and there isn't a single site with sslFlags="1" to indicates this setting is enabled. Yes I also restarted IIS.
What's going on. I'm very stumped. I'm wondering if I can completely disable SNI on the server somehow, or what would have triggered this to happen. I did several months of Windows updates yesterday, but to be frank I think it has been this way for a long time without me realizing - based on $0 in sales from IE8 XP clients ;-)
Edit:
I'm really thinking my IIS has become corrupted. When I run netsh http show sslcert every single binding is of the form IP:port. According to this article if SNI is enabled then I would see hostname:port and I see no entries in this format. There's also no entries in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\HTTP\Parameters\SslSniBindingInfo in the registry - but I confirmed that a new one is created here if I temporarily add an SNI binding.
IP:port : 10.0.0.2:443
Certificate Hash : d59a149e6678bc10d62093401c5b705cc23094be
Application ID : {4dc3e181-e14b-4a21-b022-59fc669b0914}
Certificate Store Name : My
Verify Client Certificate Revocation : Enabled
Verify Revocation Using Cached Client Certificate Only : Disabled
Usage Check : Enabled
Revocation Freshness Time : 0
URL Retrieval Timeout : 0
Ctl Identifier : (null)
Ctl Store Name : (null)
DS Mapper Usage : Disabled
Negotiate Client Certificate : Disabled