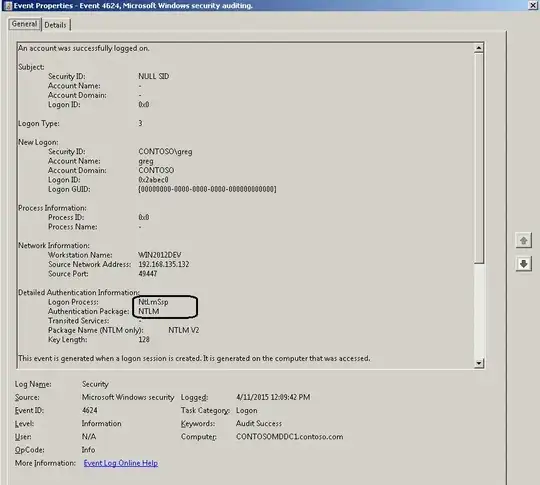
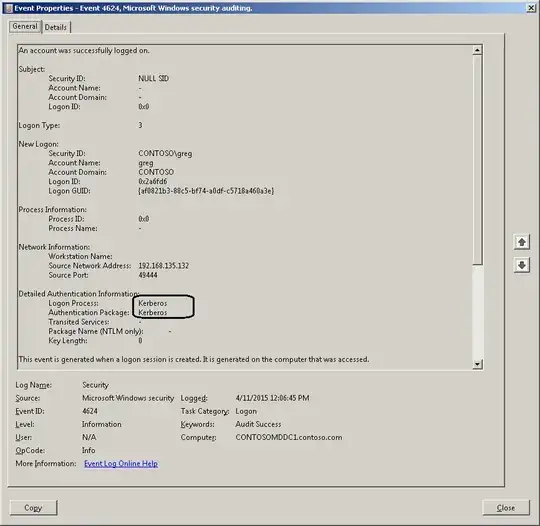
Greg's answer is alright, but your question specifically states that you want to check this from the client, not from the domain controller. So I'll take a crack at it.
First way, enable Kerberos logging on your client:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters
LogLevel DWORD 0x1
Once Kerberos logging is enabled, then, log into stuff and watch the event log. If you're using Kerberos, then you'll see the activity in the event log. If you are passing your credentials and you don't see any Kerberos activity in the event log, then you're using NTLM.
Second way, you can use the klist.exe utility to see your current Kerberos tickets. This will definitely help you if you are authenticating to a service for the first time, because you will be getting a new ticket... but for subsequent authentications to the same service, you can reuse the same ticket, and so klist.exe may be of limited use to you.
Third way, watch the authentication happen with Wireshark.