I've been playing around with StrongSwan recently as a replacement to Amazons VPN which cost money.
I'm having trouble completely configuring a IPSec tunnel between a remote server and a Ubuntu EC2 machine running StrongSwan.
My goal is to have our remote server be able to VPN into our VPC and have bi-directional access between the private subnet on AWS.
Currently, I can get a tunnel established. I can ping from the EC2 machine (running StrongSwan) to the remote OSX server. I can ping between machines in the public and private subnets in my VPC.
Currently, I cannot, ping from my OSX server to the EC2 instance on AWS running strong swan. I don't have any iptables setup to forward traffic from the EC2 (StrongSwan) machine to the other machines in my private subnet.
AWS
VPC: 10.0.0.0/16
Public Subnet: 10.0.1.0/24
Private Subnet: 10.0.2.0/24
Web EIP: 77.77.77.77 (default for VPC IGW)
VPN EIP: 66.66.66.66
AWS StrongSwan EC2
Ubuntu running StrongSwan 5.2.2
IP: 10.0.1.233
Remote Client Gateway (Cellular Modem + Gateway Combo with static IP)
Running StrongSwan 5.2.2 internally for IPSec
Public (static) IP: 55.55.55.55
LAN: 10.1.1.0/24 (DHCP Server)
Remote Client Server (OSX Machine for testing)
IP: 10.1.1.1
Network Topology
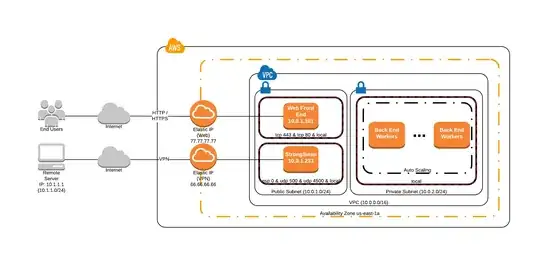
Security groups in the Public subnet wide open allowing all ICMP, UDP and TCP traffic for testing (ignore the values in the image above).
Also note the src/dst check is disabled on the StrongSwan EC2 instance
Remote Gateway StrongSwan Config (StrongSwan 5.2.2)
version 2.0
config setup
# charondebug="knl 4, asn 4, cfg 4, chd 4, dmn 4, enc 4, esp 4, ike 4, imc 4, imv 4, job 4, lib 4, mgr 4, net 4, pts 4,tls 4, tnc 4"
conn %default
keyexchange=ikev2
authby=secret
conn net-to-net
ike=aes256-sha256-modp1536,aes256-sha1-modp1536,aes128-sha256-modp1536,aes128-sha1-modp1536,3des-sha256-modp1536,3des-sha1-modp1536
esp=aes256-sha256_96-modp1536,aes256-sha1-modp1536,aes128-sha256_96-modp1536,aes128-sha1-modp1536,3des-sha256_96-modp1536,3des-sha1-modp1536
mobike=no
keyingtries=%forever
dpdaction=restart
dpddelay=5s
dpdtimeout=10s
#AWS
leftid=%any
left=10.0.1.233
leftsubnet=10.0.0.0/16
#CLIENT
rightid=%any
right=55.55.55.55
rightsubnet=10.1.1.0/24
auto=add
IPSec settings on Remote Gateway
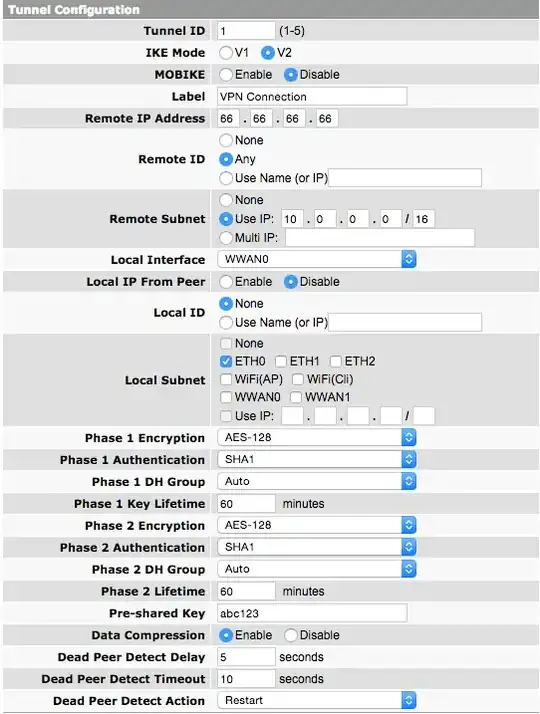
eth0 is running DHCP server with 10.1.1.0/24 CIDR block. My OSX server has IP 10.1.1.1 (on eth0)
System Logs on StrongSwan EC2
Mar 30 18:43:58 ip-10-0-1-233 charon: 00[CFG] loading secrets from '/etc/ipsec.secrets'
Mar 30 18:43:58 ip-10-0-1-233 charon: 00[CFG] loaded IKE secret for 66.66.66.66 55.55.55.55
Mar 30 18:43:58 ip-10-0-1-233 charon: 00[LIB] loaded plugins: charon test-vectors aes rc2 sha1 sha2 md4 md5 random nonce x509 revocation constraints pkcs1 pkcs7 pkcs8 pkcs12 pem openssl xcbc cmac hmac ctr ccm gcm attr kernel-netlink resolve socket-default stroke updown eap-identity addrblock
Mar 30 18:43:58 ip-10-0-1-233 charon: 00[LIB] unable to load 5 plugin features (5 due to unmet dependencies)
Mar 30 18:43:58 ip-10-0-1-233 charon: 00[LIB] dropped capabilities, running as uid 0, gid 0
Mar 30 18:43:58 ip-10-0-1-233 charon: 00[JOB] spawning 16 worker threads
Mar 30 18:43:58 ip-10-0-1-233 charon: 10[CFG] received stroke: add connection 'net-to-net'
Mar 30 18:43:58 ip-10-0-1-233 charon: 10[CFG] added configuration 'net-to-net'
Mar 30 18:44:01 ip-10-0-1-233 charon: 00[DMN] signal of type SIGINT received. Shutting down
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[DMN] Starting IKE charon daemon (strongSwan 5.1.2, Linux 3.13.0-44-generic, x86_64)
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[CFG] loading ca certificates from '/etc/ipsec.d/cacerts'
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[CFG] loading aa certificates from '/etc/ipsec.d/aacerts'
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[CFG] loading ocsp signer certificates from '/etc/ipsec.d/ocspcerts'
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[CFG] loading attribute certificates from '/etc/ipsec.d/acerts'
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[CFG] loading crls from '/etc/ipsec.d/crls'
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[CFG] loading secrets from '/etc/ipsec.secrets'
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[CFG] loaded IKE secret for 66.66.66.66 55.55.55.55
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[LIB] loaded plugins: charon test-vectors aes rc2 sha1 sha2 md4 md5 random nonce x509 revocation constraints pkcs1 pkcs7 pkcs8 pkcs12 pem openssl xcbc cmac hmac ctr ccm gcm attr kernel-netlink resolve socket-default stroke updown eap-identity addrblock
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[LIB] unable to load 5 plugin features (5 due to unmet dependencies)
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[LIB] dropped capabilities, running as uid 0, gid 0
Mar 30 18:44:07 ip-10-0-1-233 charon: 00[JOB] spawning 16 worker threads
Mar 30 18:44:07 ip-10-0-1-233 charon: 10[CFG] received stroke: add connection 'net-to-net'
Mar 30 18:44:07 ip-10-0-1-233 charon: 10[CFG] added configuration 'net-to-net'
Mar 30 18:44:17 ip-10-0-1-233 charon: 11[NET] received packet: from 55.55.55.55[500] to 10.0.1.233[500] (660 bytes)
Mar 30 18:44:17 ip-10-0-1-233 charon: 11[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
Mar 30 18:44:17 ip-10-0-1-233 charon: 11[IKE] 55.55.55.55 is initiating an IKE_SA
Mar 30 18:44:17 ip-10-0-1-233 charon: 11[IKE] local host is behind NAT, sending keep alives
Mar 30 18:44:17 ip-10-0-1-233 charon: 11[IKE] DH group MODP_2048 inacceptable, requesting MODP_1536
Mar 30 18:44:17 ip-10-0-1-233 charon: 11[ENC] generating IKE_SA_INIT response 0 [ N(INVAL_KE) ]
Mar 30 18:44:17 ip-10-0-1-233 charon: 11[NET] sending packet: from 10.0.1.233[500] to 55.55.55.55[500] (38 bytes)
Mar 30 18:44:17 ip-10-0-1-233 charon: 12[NET] received packet: from 55.55.55.55[500] to 10.0.1.233[500] (596 bytes)
Mar 30 18:44:17 ip-10-0-1-233 charon: 12[ENC] parsed IKE_SA_INIT request 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) ]
Mar 30 18:44:17 ip-10-0-1-233 charon: 12[IKE] 55.55.55.55 is initiating an IKE_SA
Mar 30 18:44:17 ip-10-0-1-233 charon: 12[IKE] local host is behind NAT, sending keep alives
Mar 30 18:44:17 ip-10-0-1-233 charon: 12[ENC] generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) N(MULT_AUTH) ]
Mar 30 18:44:17 ip-10-0-1-233 charon: 12[NET] sending packet: from 10.0.1.233[500] to 55.55.55.55[500] (376 bytes)
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[NET] received packet: from 55.55.55.55[4500] to 10.0.1.233[4500] (336 bytes)
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[ENC] parsed IKE_AUTH request 1 [ IDi AUTH N(IPCOMP_SUP) SA TSi TSr N(MULT_AUTH) N(EAP_ONLY) ]
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[CFG] looking for peer configs matching 10.0.1.233[%any]...55.55.55.55[55.55.55.55]
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[CFG] selected peer config 'net-to-net'
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[IKE] authentication of '55.55.55.55' with pre-shared key successful
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[CFG] no IDr configured, fall back on IP address
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[IKE] authentication of '10.0.1.233' (myself) with pre-shared key
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[IKE] IKE_SA net-to-net[2] established between 10.0.1.233[10.0.1.233]...55.55.55.55[55.55.55.55]
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[IKE] scheduling reauthentication in 10081s
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[IKE] maximum IKE_SA lifetime 10621s
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[IKE] received IPCOMP_SUPPORTED notify but IPComp is disabled, ignoring
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[IKE] CHILD_SA net-to-net{1} established with SPIs c2a08785_i cc1db76f_o and TS 10.0.1.0/24 === 10.1.1.0/24
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[ENC] generating IKE_AUTH response 1 [ IDr AUTH SA TSi TSr N(AUTH_LFT) ]
Mar 30 18:44:18 ip-10-0-1-233 charon: 13[NET] sending packet: from 10.0.1.233[4500] to 55.55.55.55[4500] (224 bytes)
Mar 30 18:44:23 ip-10-0-1-233 charon: 14[IKE] sending DPD request
tpcdump on AWS side when remote connects
18:41:14.660917 IP mobile-55-55-55-55.mycingular.net.isakmp > ip-10-0-1-233.ec2.internal.isakmp: isakmp: parent_sa ikev2_init[I]
18:41:14.681096 IP ip-10-0-1-233.ec2.internal.isakmp > mobile-55-55-55-55.mycingular.net.isakmp: isakmp: parent_sa ikev2_init[R]
18:41:15.259862 IP mobile-55-55-55-55.mycingular.net.isakmp > ip-10-0-1-233.ec2.internal.isakmp: isakmp: parent_sa ikev2_init[I]
18:41:15.271718 IP ip-10-0-1-233.ec2.internal.isakmp > mobile-55-55-55-55.mycingular.net.isakmp: isakmp: parent_sa ikev2_init[R]
18:41:15.809157 IP mobile-55-55-55-55.mycingular.net.ipsec-nat-t > ip-10-0-1-233.ec2.internal.ipsec-nat-t: NONESP-encap: isakmp: child_sa ikev2_auth[I]
18:41:15.813883 IP ip-10-0-1-233.ec2.internal.ipsec-nat-t > mobile-55-55-55-55.mycingular.net.ipsec-nat-t: NONESP-encap: isakmp: child_sa ikev2_auth[R]
18:41:20.812881 IP ip-10-0-1-233.ec2.internal.ipsec-nat-t > mobile-55-55-55-55.mycingular.net.ipsec-nat-t: NONESP-encap: isakmp: parent_sa inf2
18:41:21.139689 IP mobile-55-55-55-55.mycingular.net.ipsec-nat-t > ip-10-0-1-233.ec2.internal.ipsec-nat-t: NONESP-encap: isakmp: child_sa inf2[I]
18:41:21.140103 IP ip-10-0-1-233.ec2.internal.ipsec-nat-t > mobile-55-55-55-55.mycingular.net.ipsec-nat-t: NONESP-encap: isakmp: child_sa inf2[R]
18:41:21.289057 IP mobile-55-55-55-55.mycingular.net.ipsec-nat-t > ip-10-0-1-233.ec2.internal.ipsec-nat-t: NONESP-encap: isakmp: parent_sa inf2[IR]
18:41:26.088336 IP mobile-55-55-55-55.mycingular.net.ipsec-nat-t > ip-10-0-1-233.ec2.internal.ipsec-nat-t: NONESP-encap: isakmp: child_sa inf2[I]
18:41:26.088827 IP ip-10-0-1-233.ec2.internal.ipsec-nat-t > mobile-55-55-55-55.mycingular.net.ipsec-nat-t: NONESP-encap: isakmp: child_sa inf2[R]
18:41:31.103016 IP mobile-55-55-55-55.mycingular.net.ipsec-nat-t > ip-10-0-1-233.ec2.internal.ipsec-nat-t: NONESP-encap: isakmp: child_sa inf2[I]
18:41:31.103931 IP ip-10-0-1-233.ec2.internal.ipsec-nat-t > mobile-55-55-55-55.mycingular.net.ipsec-nat-t: NONESP-encap: isakmp: child_sa inf2[R]
I believe my setup is close but I'm missing something fundamental. Any ideas why my tunnel is not working bi-directionally? I can ping from AWS->Remote but not the other way around. Note: I do not have ip forwarding or any custom iptable rules setup on the Ubuntu (StrongSwan) EC2 instance.
Note: There is also this document created by the StrongSwan folks which I've looked at and attempted to implement with less luck than my current setup.