Complete noob here. Please be gentle :)
I have a Windows 2008 server, running hMailServer. Right now all my communication is unencrypted. I want to start using TLS. So now I've got myself a SSL certificate for my domain. This I did by creating a certificate request in IIS, which I uploaded to a CA (StartSSL, FWIW). I then downloaded and saved the certificate file in IIS.
Then I followed the hMailServer instructions, which helpfully told me to create a new SSL certificate, but...
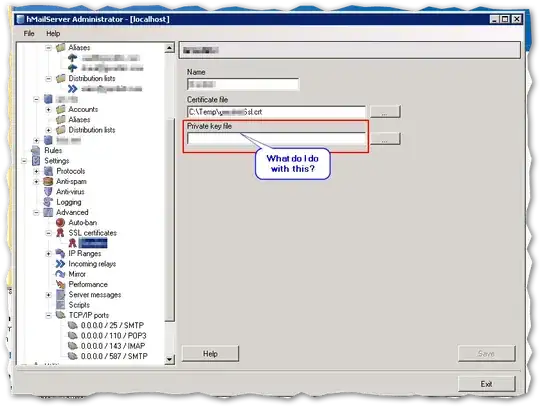
So where do I get this private key file from?
UPDATE: It turns out there are two ways to generate a SSL certificate:
- Generate a certificate request in IIS and upload this to the CA, which in turn generates a certificate (this is what I did first); OR
- Enter a password on the CA site, and they then generate for you both a Private Key and a SSL certificate.
So now I have a private key. But now that I have filled in all the necessary information to set up my SSL Certificate in hMailServer, I then bind the port to the certificate... and it doesn't work. To the outside world, this previously working port now appears closed (verified on CanYouSeeMe.org).
What trick am I missing now?