I am by no means an expert when it comes to networking, I've inherited one which I am pretty much sure is wrong and due to my lack of experience I have no idea how to clean it up.
The network looks like this simplified:
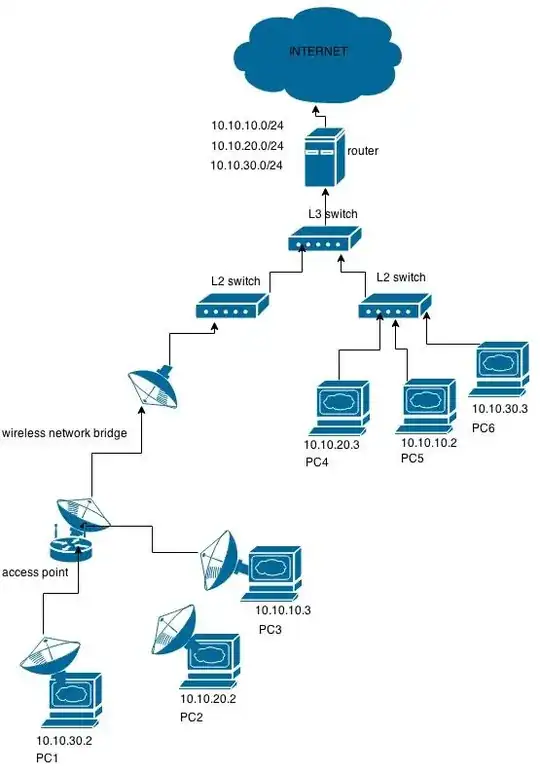
L2 switches have multiple devices connected to them.
Some devices act as wireless bridges that connect to access points that then get connected to wirelessly by clients.
The important part is that each L2 switch consists of multiple subnets. In this example
- 10.10.10.0/24
- 10.10.20.0/24
- 10.10.30.0/24
Devices that are part of these networks are scattered randomly, but eventually end up at one of the L2 switches.
I am seeing behaviour such as unicast flooding. (E.g in wireshark, if I am at PC5)
not eth.addr == <MY_MAC_ADDRESS> and ip.addr != 10.10.10.2 and ip.addr != 10.10.10.255
I can see traffic from or destined to other networks (10.10.20.0/24 and 10.10.30.0.24) - even if the hosts are located in the other L2 switch.
Not to mention that this has a negative impact on the router which can be felt especially at peak hours (bandwidth dropping eratically).
The only safety measure implemented on the switches is Port Isolation, but I don't think it's doing it's job.
What I could do to improve the situation?
Are VLANs out of the question because subnets are scattered on the L2 switches?
I can remotely change clients (that connect wirelessly) to use PPPOE protocol, but would this help with such unicast flooding?
What would you suggest?