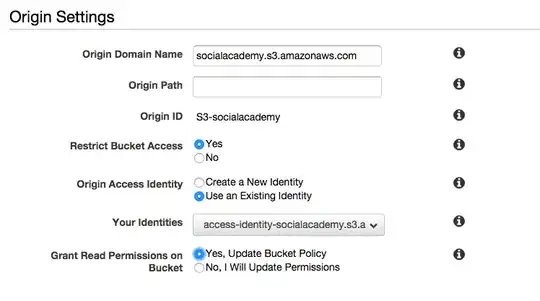
I have one account with privilege to manage S3 (S3_User), and another one to manage Cloud Front (Cloud_Front_User).
Now, I've created a bucket "bucketname" with S3_User and a distribution with Cloud_Front_User with origin my S3 Bucket.
When I tried to access a resource through Cloudfront I get this
<Error>
<Code>AccessDenied</Code>
<Message>Access Denied</Message>
<RequestId>555667558C0B2698</RequestId>
<HostId>
QP0y2/XTsJqItm815aDsdoLTF853zMeEPUAykvxjzdFfU1WwfXHioa6CeLWmc96RDVJopBu+eLE=
</HostId>
</Error>
I've set this: http://cl.ly/image/1s0I1H3A3p1N
but when I click on "Save", after some time I get an error message saying that it wasn't able to set identity on the S3 bucket. I think this is because I manage CLoudFront with "Cloud_Front_User" and S3 with "S3_User". So, how could I manually set S3 policy on the bucket to allow CloudFront to access s3?
S3 Bucket policy
{
"Version": "2012-10-17",
"Id": "PolicyForCloudFrontPrivateContent",
"Statement": [
{
"Sid": " Grant a CloudFront Origin Identity access to support private content",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::cloudfront:user/CloudFront Origin Access Identity E780000000000"
},
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::socialacademy/*"
}
]
}