One of our IIS servers (IIS 7.5, Server 2008 R2) is apparently "vulnerable" to the tilde Short Filename disclosure issue.
However, I'm having a hard time actually fixing the issue. So far, I've
Disabled 8.3 filenames, stopped the web server, recreated the site directory and started the service again
Added a filter rule for a tilde in the URL:
- Added a filter rule for a tilde ANYWHERE:

IISRESETa couple of timesChecked that
web.confighas the relevant filter rules added
.. but still, I can't get my site to pass the test :
java -jar ~/temp/IIS-ShortName-Scanner-master/IIS_shortname_scanner.jar http://www.example.com
[...SNIP...]
Testing request method: "TRACE" with magic part: "/webresource.axd" ...
Testing request method: "DEBUG" with magic part: "" ...
Testing request method: "OPTIONS" with magic part: "" ...
Testing request method: "GET" with magic part: "" ...
Reliable request method was found = GET
Reliable magic part was found =
144 requests have been sent to the server:
<<< The target website is vulnerable! >>>
What else do I need to do to resolve this?
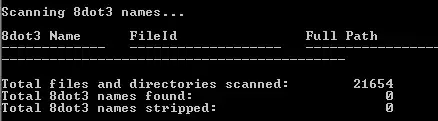
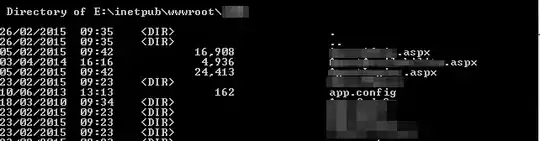
EDIT: here's DIR /x which appears to show no 8.3 filenames:
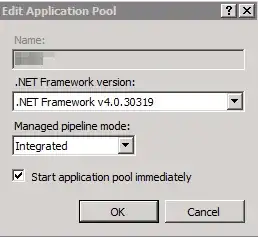
and here's the app pool for the site (all other sites on the server are the same):
EDIT2: Verification there's no 8.3 filenames left: