Refer to the documentation
Cloudflare's docs are fairly clear on this. Obviously (it should be obvious) Flexible ssl means the connection from cloudflare to the origin is unencrypted.
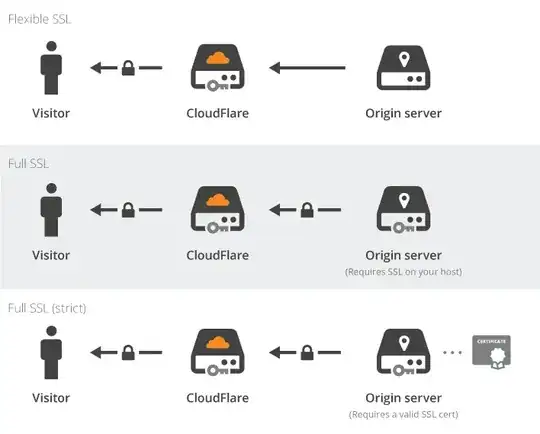
For full ssl (either permutation) the following applies:
Encrypts the connection between your site visitors and CloudFlare, and from CloudFlare to your server.
They are two different connections, So the answer to "Does cloudflare know the decrypted content?" is: "Yes".
Note that for EV or OV SSL certificates - you need to uploaded them to to cloudflare for end-users to see them, it's still 2 connections - not end-to-end encryption.
Reasons to use SSL
Using ssl prevents MITM attacks, it doesn't mean the cdn you're using is oblivious to the content it's serving, for you. You should maybe ask yourself why you want to encrypt the connection.
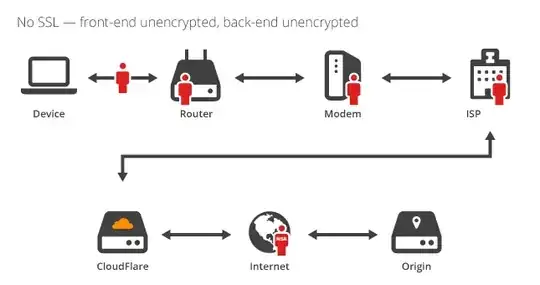
With no SSL, there are plenty of places a MITM attack can occur:
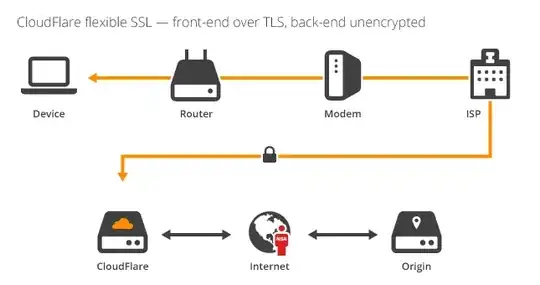
With Flexible SSL - that eliminates most, but not all of them:
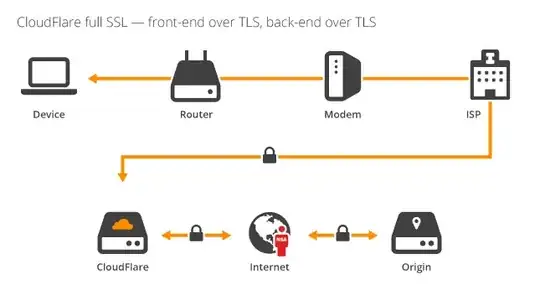
With Full SSL - there's still the possibility of a MITM attack:
With Full SSL (Strict) - a MITM attack is now not possible without cloudflare itself being compromised:
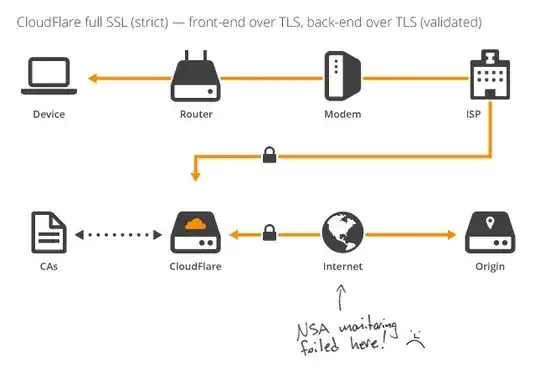
If you are concerned that cloudflare can read your data - don't use cloudflare.




