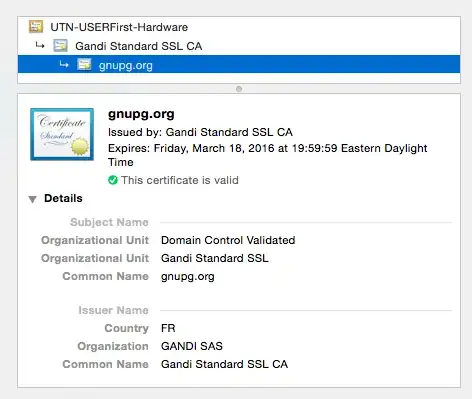
I came across this question and noticed I had answered something similar here: https://stackoverflow.com/questions/7885785/using-openssl-to-get-the-certificate-from-a-server/68277430#68277430
I also had the same challenge and next to that I discovered that openssl doesn't return the root ca. I have built an alternative for specifically for this purpose which might be useful for other developers, see here: GitHub - Certificate ripper
Command
crip print -u=https://gnupg.org
Output
Certificates for url = https://gnupg.org
[
[
Version: V3
Subject: CN=gnupg.org
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
params: null
modulus: 31584528901574007750301020287561448010695338445786656836820202222425310660293397103661612041262534815824710633384445406661552999674139683313292182907220124973641103147823211675629863952189464092250334775320079482164648964670152919444386631405421166704969790376810530092741753755204051610269112728244627288812180893123949732920362020211922819834221347165888182335229776214076417362141617456849548559339712503046241890787857054712025639768795686815610181667002438461217925898165006378013013126800098621764184263923324590864316888475244387674964001095520567493168508649309644487636171722874605322088933794460410194036701
public exponent: 65537
Validity: [From: Sat Mar 05 01:55:18 CET 2022,
To: Fri Jun 03 02:55:17 CEST 2022]
Issuer: CN=R3, O=Let's Encrypt, C=US
SerialNumber: [ 04b186e2 062aebcc b4c9ae1b 10c1777c c520]
Certificate Extensions: 9
[1]: ObjectId: 1.3.6.1.4.1.11129.2.4.2 Criticality=false
Extension unknown: DER encoded OCTET string =
0000: 04 81 F5 04 81 F2 00 F0 00 76 00 DF A5 5E AB 68 .........v...^.h
0010: 82 4F 1F 6C AD EE B8 5F 4E 3E 5A EA CD A2 12 A4 .O.l..._N>Z.....
0020: 6A 5E 8E 3B 12 C0 20 44 5C 2A 73 00 00 01 7F 57 j^.;.. D\*s....W
0030: C9 D0 37 00 00 04 03 00 47 30 45 02 21 00 92 05 ..7.....G0E.!...
0040: 73 F3 19 12 C5 C3 0B 97 95 B3 C4 3B 65 46 C5 6C s..........;eF.l
0050: 60 C4 61 52 77 0D 8C D7 CD 96 DE 82 87 B9 02 20 `.aRw..........
0060: 64 48 71 14 C4 11 95 3C 68 13 91 46 4F 72 77 01 dHq....<h..FOrw.
0070: FB 7F C8 8B 59 96 BD 2C 4B EA 51 61 8C 29 34 6A ....Y..,K.Qa.)4j
0080: 00 76 00 29 79 BE F0 9E 39 39 21 F0 56 73 9F 63 .v.)y...99!.Vs.c
0090: A5 77 E5 BE 57 7D 9C 60 0A F8 F9 4D 5D 26 5C 25 .w..W..`...M]&\%
00A0: 5D C7 84 00 00 01 7F 57 C9 D0 27 00 00 04 03 00 ]......W..'.....
00B0: 47 30 45 02 21 00 BD 4F C9 94 6A 0C 57 0F DF D8 G0E.!..O..j.W...
00C0: 10 8A 0C 09 35 31 30 AF CE B6 8E B8 00 BC 4F 46 ....510.......OF
00D0: 56 91 C1 83 AF 20 02 20 3C 61 37 B3 09 AF EF 40 V.... . <a7....@
00E0: 22 F7 43 1F 46 07 EE AA FC 3D A4 0E 3A 60 A5 E1 ".C.F....=..:`..
00F0: 95 E3 0B B3 30 0D 7E 78 ....0..x
[2]: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: ocsp
accessLocation: URIName: http://r3.o.lencr.org
,
accessMethod: caIssuers
accessLocation: URIName: http://r3.i.lencr.org/
]
]
[3]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 14 2E B3 17 B7 58 56 CB AE 50 09 40 E6 1F AF 9D .....XV..P.@....
0010: 8B 14 C2 C6 ....
]
]
[4]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:false
PathLen: undefined
]
[5]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 1A 68 74 74 70 3A 2F 2F 63 70 73 2E 6C 65 74 ..http://cps.let
0010: 73 65 6E 63 72 79 70 74 2E 6F 72 67 sencrypt.org
]] ]
]
[6]: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
serverAuth
clientAuth
]
[7]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_Encipherment
]
[8]: ObjectId: 2.5.29.17 Criticality=false
SubjectAlternativeName [
DNSName: gnupg.org
DNSName: www.gnupg.org
]
[9]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 02 99 E2 B9 65 0A 77 F2 E5 9A 73 CE 9C 55 AF 7F ....e.w...s..U..
0010: 5B AE BE 65 [..e
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 31 75 50 29 45 66 2B FA 52 F4 85 C3 E7 62 5F 09 1uP)Ef+.R....b_.
0010: 8C A9 18 3C 8E 4F 5A 4A B2 B8 65 05 E0 2D 62 51 ...<.OZJ..e..-bQ
0020: 15 91 A2 78 A3 2A B6 B8 1F FD C8 D7 75 D2 98 E1 ...x.*......u...
0030: 2E 87 43 24 0C 38 60 E8 73 76 6C E4 7F 6C 3A DF ..C$.8`.svl..l:.
0040: 56 5D AB DB B8 7F F7 F3 6C 43 AA CA A3 97 BF 32 V]......lC.....2
0050: D1 8C 20 D1 85 EB 43 DA 82 A9 08 DA 6C 2C CB CC .. ...C.....l,..
0060: 75 8C D6 E8 A1 EA DF 82 E9 0C 33 B7 C9 0E 59 14 u.........3...Y.
0070: 9F 6D 4E 7E 6F BF 6B A9 F6 4C 82 19 48 9A 6F 8B .mN.o.k..L..H.o.
0080: BE E7 F7 80 6F F6 15 AD 56 11 1C F1 7E C1 F4 CF ....o...V.......
0090: C4 B7 5F C7 9F C0 0E 5A 47 46 AB FE 39 F3 7C 37 .._....ZGF..9..7
00A0: 2D 90 DE B5 5F F9 DE 51 E4 29 6F CA 6E C6 7A 21 -..._..Q.)o.n.z!
00B0: 00 3F 66 D0 24 06 77 73 5C 47 AD 4F D9 87 C7 FF .?f.$.ws\G.O....
00C0: 93 0C 1B 27 A8 6D 53 DF AC EF A3 54 C7 84 46 8F ...'.mS....T..F.
00D0: EF BD 80 71 FD A4 6F 6B 06 37 9C 0A 96 14 16 04 ...q..ok.7......
00E0: F2 66 B5 80 D0 53 2C 73 3B 36 EE DC DE 59 37 52 .f...S,s;6...Y7R
00F0: 37 DA E6 A9 BA 83 A3 1D EF B7 DC 1E 00 91 15 B3 7...............
]
========== NEXT CERTIFICATE FOR https://gnupg.org ==========
[
[
Version: V3
Subject: CN=R3, O=Let's Encrypt, C=US
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
params: null
modulus: 23607590023527405233483514815960094733025362836439268915823566209453533788829410729612693188664033965601284889382200672291623712219351579442466292134025779170871903029675641332227720513370499414392174777629378433333281492782006644003508406669842374574620445942041275265465205367002253387972103578862358103547035353751037986892891938939537013712276962031758303128178118156019997818459064793797705051611931042977322694991611263911077235433119719504206173897534215486225391156231168313218127765624386188467360149426877213161912342004781300247624712380387337803861727744706241919394251136381590874774264144198228326996757
public exponent: 65537
Validity: [From: Fri Sep 04 02:00:00 CEST 2020,
To: Mon Sep 15 18:00:00 CEST 2025]
Issuer: CN=ISRG Root X1, O=Internet Security Research Group, C=US
SerialNumber: [ 912b084a cf0c18a7 53f6d62e 25a75f5a]
Certificate Extensions: 8
[1]: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://x1.i.lencr.org/
]
]
[2]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: 79 B4 59 E6 7B B6 E5 E4 01 73 80 08 88 C8 1A 58 y.Y......s.....X
0010: F6 E9 9B 6E ...n
]
]
[3]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:0
]
[4]: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://x1.c.lencr.org/]
]]
[5]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[] ]
]
[6]: ObjectId: 2.5.29.37 Criticality=false
ExtendedKeyUsages [
clientAuth
serverAuth
]
[7]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
DigitalSignature
Key_CertSign
Crl_Sign
]
[8]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 14 2E B3 17 B7 58 56 CB AE 50 09 40 E6 1F AF 9D .....XV..P.@....
0010: 8B 14 C2 C6 ....
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 85 CA 4E 47 3E A3 F7 85 44 85 BC D5 67 78 B2 98 ..NG>...D...gx..
0010: 63 AD 75 4D 1E 96 3D 33 65 72 54 2D 81 A0 EA C3 c.uM..=3erT-....
0020: ED F8 20 BF 5F CC B7 70 00 B7 6E 3B F6 5E 94 DE .. ._..p..n;.^..
0030: E4 20 9F A6 EF 8B B2 03 E7 A2 B5 16 3C 91 CE B4 . ..........<...
0040: ED 39 02 E7 7C 25 8A 47 E6 65 6E 3F 46 F4 D9 F0 .9...%.G.en?F...
0050: CE 94 2B EE 54 CE 12 BC 8C 27 4B B8 C1 98 2F A2 ..+.T....'K.../.
0060: AF CD 71 91 4A 08 B7 C8 B8 23 7B 04 2D 08 F9 08 ..q.J....#..-...
0070: 57 3E 83 D9 04 33 0A 47 21 78 09 82 27 C3 2A C8 W>...3.G!x..'.*.
0080: 9B B9 CE 5C F2 64 C8 C0 BE 79 C0 4F 8E 6D 44 0C ...\.d...y.O.mD.
0090: 5E 92 BB 2E F7 8B 10 E1 E8 1D 44 29 DB 59 20 ED ^.........D).Y .
00A0: 63 B9 21 F8 12 26 94 93 57 A0 1D 65 04 C1 0A 22 c.!..&..W..e..."
00B0: AE 10 0D 43 97 A1 18 1F 7E E0 E0 86 37 B5 5A B1 ...C........7.Z.
00C0: BD 30 BF 87 6E 2B 2A FF 21 4E 1B 05 C3 F5 18 97 .0..n+*.!N......
00D0: F0 5E AC C3 A5 B8 6A F0 2E BC 3B 33 B9 EE 4B DE .^....j...;3..K.
00E0: CC FC E4 AF 84 0B 86 3F C0 55 43 36 F6 68 E1 36 .......?.UC6.h.6
00F0: 17 6A 8E 99 D1 FF A5 40 A7 34 B7 C0 D0 63 39 35 .j.....@.4...c95
0100: 39 75 6E F2 BA 76 C8 93 02 E9 A9 4B 6C 17 CE 0C 9un..v.....Kl...
0110: 02 D9 BD 81 FB 9F B7 68 D4 06 65 B3 82 3D 77 53 .......h..e..=wS
0120: F8 8E 79 03 AD 0A 31 07 75 2A 43 D8 55 97 72 C4 ..y...1.u*C.U.r.
0130: 29 0E F7 C4 5D 4E C8 AE 46 84 30 D7 F2 85 5F 18 )...]N..F.0..._.
0140: A1 79 BB E7 5E 70 8B 07 E1 86 93 C3 B9 8F DC 61 .y..^p.........a
0150: 71 25 2A AF DF ED 25 50 52 68 8B 92 DC E5 D6 B5 q%*...%PRh......
0160: E3 DA 7D D0 87 6C 84 21 31 AE 82 F5 FB B9 AB C8 .....l.!1.......
0170: 89 17 3D E1 4C E5 38 0E F6 BD 2B BD 96 81 14 EB ..=.L.8...+.....
0180: D5 DB 3D 20 A7 7E 59 D3 E2 F8 58 F9 5B B8 48 CD ..= ..Y...X.[.H.
0190: FE 5C 4F 16 29 FE 1E 55 23 AF C8 11 B0 8D EA 7C .\O.)..U#.......
01A0: 93 90 17 2F FD AC A2 09 47 46 3F F0 E9 B0 B7 FF .../....GF?.....
01B0: 28 4D 68 32 D6 67 5E 1E 69 A3 93 B8 F5 9D 8B 2F (Mh2.g^.i....../
01C0: 0B D2 52 43 A6 6F 32 57 65 4D 32 81 DF 38 53 85 ..RC.o2WeM2..8S.
01D0: 5D 7E 5D 66 29 EA B8 DD E4 95 B5 CD B5 56 12 42 ].]f)........V.B
01E0: CD C4 4E C6 25 38 44 50 6D EC CE 00 55 18 FE E9 ..N.%8DPm...U...
01F0: 49 64 D4 4E CA 97 9C B4 5B C0 73 A8 AB B8 47 C2 Id.N....[.s...G.
]
========== NEXT CERTIFICATE FOR https://gnupg.org ==========
[
[
Version: V3
Subject: CN=ISRG Root X1, O=Internet Security Research Group, C=US
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 4096 bits
params: null
modulus: 709477870415445373015359016562426660610553770685944520893298396600226760899977879191004898543350831842119174188613678136510262472550532722234131754439181090009824131001234702144200501816519311599904090606194984753842587622398776018408050245574116028550608708896478977104703101364577377554823893350339376892984086676842821506637376561471221178677513035811884589888230947855482554780924844280661412982827405878164907670403886160896655313460186264922042760067692235383478494519985672059698752915965998412445946254227413232257276525240006651483130792248112417425846451951438781260632137645358927568158361961710185115502577127010922344394993078948994750404287047493247048147066090211292167313905862438457453781042040498702821432013765502024105065778257759178356925494156447570322373310256999609083201778278588599854706241788119448943034477370959349516873162063461521707809689839710972753590949570167489887658749686740890549110678989462474318310617765270337415238713770800711236563610171101328052424145478220993016515262478543813796899677215192789612682845145008993144513547444131126029557147570005369943143213525671105288817016183804256755470528641042403865830064493168693765438364296560479053823886598989258655438933191724193029337334607
public exponent: 65537
Validity: [From: Wed Jan 20 20:14:03 CET 2021,
To: Mon Sep 30 20:14:03 CEST 2024]
Issuer: CN=DST Root CA X3, O=Digital Signature Trust Co.
SerialNumber: [ 40017721 37d4e942 b8ee76aa 3c640ab7]
Certificate Extensions: 7
[1]: ObjectId: 1.3.6.1.5.5.7.1.1 Criticality=false
AuthorityInfoAccess [
[
accessMethod: caIssuers
accessLocation: URIName: http://apps.identrust.com/roots/dstrootcax3.p7c
]
]
[2]: ObjectId: 2.5.29.35 Criticality=false
AuthorityKeyIdentifier [
KeyIdentifier [
0000: C4 A7 B1 A4 7B 2C 71 FA DB E1 4B 90 75 FF C4 15 .....,q...K.u...
0010: 60 85 89 10 `...
]
]
[3]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
[4]: ObjectId: 2.5.29.31 Criticality=false
CRLDistributionPoints [
[DistributionPoint:
[URIName: http://crl.identrust.com/DSTROOTCAX3CRL.crl]
]]
[5]: ObjectId: 2.5.29.32 Criticality=false
CertificatePolicies [
[CertificatePolicyId: [2.23.140.1.2.1]
[] ]
[CertificatePolicyId: [1.3.6.1.4.1.44947.1.1.1]
[PolicyQualifierInfo: [
qualifierID: 1.3.6.1.5.5.7.2.1
qualifier: 0000: 16 22 68 74 74 70 3A 2F 2F 63 70 73 2E 72 6F 6F ."http://cps.roo
0010: 74 2D 78 31 2E 6C 65 74 73 65 6E 63 72 79 70 74 t-x1.letsencrypt
0020: 2E 6F 72 67 .org
]] ]
]
[6]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
Key_CertSign
Crl_Sign
]
[7]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: 79 B4 59 E6 7B B6 E5 E4 01 73 80 08 88 C8 1A 58 y.Y......s.....X
0010: F6 E9 9B 6E ...n
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 0A 73 00 6C 96 6E FF 0E 52 D0 AE DD 8C E7 5A 06 .s.l.n..R.....Z.
0010: AD 2F A8 E3 8F BF C9 0A 03 15 50 C2 E5 6C 42 BB ./........P..lB.
0020: 6F 9B F4 B4 4F C2 44 88 08 75 CC EB 07 9B 14 62 o...O.D..u.....b
0030: 6E 78 DE EC 27 BA 39 5C F5 A2 A1 6E 56 94 70 10 nx..'.9\...nV.p.
0040: 53 B1 BB E4 AF D0 A2 C3 2B 01 D4 96 F4 C5 20 35 S.......+..... 5
0050: 33 F9 D8 61 36 E0 71 8D B4 B8 B5 AA 82 45 95 C0 3..a6.q......E..
0060: F2 A9 23 28 E7 D6 A1 CB 67 08 DA A0 43 2C AA 1B ..#(....g...C,..
0070: 93 1F C9 DE F5 AB 69 5D 13 F5 5B 86 58 22 CA 4D ......i]..[.X".M
0080: 55 E4 70 67 6D C2 57 C5 46 39 41 CF 8A 58 83 58 U.pgm.W.F9A..X.X
0090: 6D 99 FE 57 E8 36 0E F0 0E 23 AA FD 88 97 D0 E3 m..W.6...#......
00A0: 5C 0E 94 49 B5 B5 17 35 D2 2E BF 4E 85 EF 18 E0 \..I...5...N....
00B0: 85 92 EB 06 3B 6C 29 23 09 60 DC 45 02 4C 12 18 ....;l)#.`.E.L..
00C0: 3B E9 FB 0E DE DC 44 F8 58 98 AE EA BD 45 45 A1 ;.....D.X....EE.
00D0: 88 5D 66 CA FE 10 E9 6F 82 C8 11 42 0D FB E9 EC .]f....o...B....
00E0: E3 86 00 DE 9D 10 E3 38 FA A4 7D B1 D8 E8 49 82 .......8......I.
00F0: 84 06 9B 2B E8 6B 4F 01 0C 38 77 2E F9 DD E7 39 ...+.kO..8w....9
]
========== NEXT CERTIFICATE FOR https://gnupg.org ==========
[
[
Version: V3
Subject: CN=DST Root CA X3, O=Digital Signature Trust Co.
Signature Algorithm: SHA1withRSA, OID = 1.2.840.113549.1.1.5
Key: Sun RSA public key, 2048 bits
params: null
modulus: 28237887677026032203151777657129561581522073060401233851894187952595640780665579499663841407267510759260214748789212535957135845654219821366017427323985352100172211628961551647178765278465245040619994286316630852210928184346090961906367138096715766033171261107313432772299467819936678634109708967378829013418649505942485529500580167736159568208924601034682852941882633722952597854385181938557682865139545636282689862459897027632511916072421459210380987954549724536623494064393973052186448977570989493998685404014473715688796607543139914669307234440905936555495044671225489918726010863829142065064843131427399159251549
public exponent: 65537
Validity: [From: Sat Sep 30 23:12:19 CEST 2000,
To: Thu Sep 30 16:01:15 CEST 2021]
Issuer: CN=DST Root CA X3, O=Digital Signature Trust Co.
SerialNumber: [ 44afb080 d6a327ba 89303986 2ef8406b]
Certificate Extensions: 3
[1]: ObjectId: 2.5.29.19 Criticality=true
BasicConstraints:[
CA:true
PathLen:2147483647
]
[2]: ObjectId: 2.5.29.15 Criticality=true
KeyUsage [
Key_CertSign
Crl_Sign
]
[3]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: C4 A7 B1 A4 7B 2C 71 FA DB E1 4B 90 75 FF C4 15 .....,q...K.u...
0010: 60 85 89 10 `...
]
]
]
Algorithm: [SHA1withRSA]
Signature:
0000: A3 1A 2C 9B 17 00 5C A9 1E EE 28 66 37 3A BF 83 ..,...\...(f7:..
0010: C7 3F 4B C3 09 A0 95 20 5D E3 D9 59 44 D2 3E 0D .?K.... ]..YD.>.
0020: 3E BD 8A 4B A0 74 1F CE 10 82 9C 74 1A 1D 7E 98 >..K.t.....t....
0030: 1A DD CB 13 4B B3 20 44 E4 91 E9 CC FC 7D A5 DB ....K. D........
0040: 6A E5 FE E6 FD E0 4E DD B7 00 3A B5 70 49 AF F2 j.....N...:.pI..
0050: E5 EB 02 F1 D1 02 8B 19 CB 94 3A 5E 48 C4 18 1E ..........:^H...
0060: 58 19 5F 1E 02 5A F0 0C F1 B1 AD A9 DC 59 86 8B X._..Z.......Y..
0070: 6E E9 91 F5 86 CA FA B9 66 33 AA 59 5B CE E2 A7 n.......f3.Y[...
0080: 16 73 47 CB 2B CC 99 B0 37 48 CF E3 56 4B F5 CF .sG.+...7H..VK..
0090: 0F 0C 72 32 87 C6 F0 44 BB 53 72 6D 43 F5 26 48 ..r2...D.SrmC.&H
00A0: 9A 52 67 B7 58 AB FE 67 76 71 78 DB 0D A2 56 14 .Rg.X..gvqx...V.
00B0: 13 39 24 31 85 A2 A8 02 5A 30 47 E1 DD 50 07 BC .9$1....Z0G..P..
00C0: 02 09 90 00 EB 64 63 60 9B 16 BC 88 C9 12 E6 D2 .....dc`........
00D0: 7D 91 8B F9 3D 32 8D 65 B4 E9 7C B1 57 76 EA C5 ....=2.e....Wv..
00E0: B6 28 39 BF 15 65 1C C8 F6 77 96 6A 0A 8D 77 0B .(9..e...w.j..w.
00F0: D8 91 0B 04 8E 07 DB 29 B6 0A EE 9D 82 35 35 10 .......).....55.
]