We recently reissued our GoDaddy wildcard cert with the SHA256 signing algorithm (FYI they still revoke the old cert in 72 hours even if you don't re-key it, so you should re-key anyway). We use this cert for our RemoteApps, Terminal Servers' RDP, RDGateway, and RDWeb (IIS).
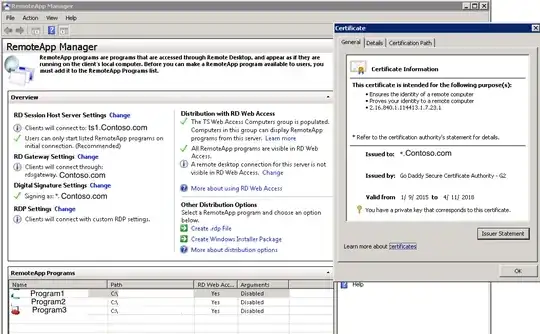
When I change to the new wildcard certificate in the "RemoteApp Manager"->"Digital Signature Settings" on a given Terminal Server (AKA Session Host server) Connections from RDWeb for apps published on that terminal server fail for some users, but connections using the a .rdp file work fine for all users. Furthermore, and this is the strangest thing I have ever seen, the wrong user is logged as being denied access at the gateway. If I change the certificate back to the old, revoked cert for this one setting, then everything works.
Working Setup:
- All Windows 2008 R2 Datacenter servers
- RDGateway+RDWeb - rdsgateway.contoso.com (new wildcard cert installed for both IIS and rdgateway)
- TS - ts1.contoso.com (new wildcard cert installed only for RDP, OLD cert installed for RemoteAPP)
Non-working Setup:
- All Windows 2008 R2 Datacenter servers
- RDGateway+RDWeb - rdsgateway.contoso.com (new wildcard cert installed for both IIS and rdgateway)
- TS - ts1.contoso.com (new wildcard cert installed for RDP, NEW cert installed for RemoteAPP)
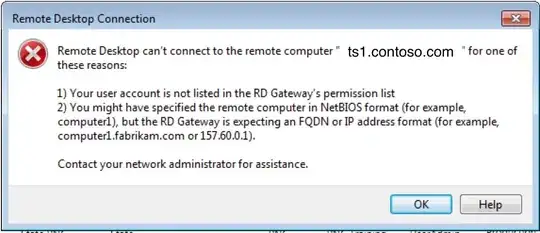
When Launching from RDWeb using user "CONTOSO\bob" the following error is generated:
Remote Desktop can't connect to the remote computer "ts1.contoso.com" for one of these reasons: 1) Your user account is not listed in the RD Gateway's permission list 2) you might have specified the remote computer in NetBIOS format...
When I look at the Event log "Microsoft-Windows-TerminalServices-Gateway/Operational" I see the following error:
The user "CONTOSO\alice", on client computer "123.123.123.123", did not meet resource authorization policy requirements and was therefore not authorized to resource "ts1.contoso.com". The following error occurred: "23002".
What is going on? Why does changing the RemoteApp's signing cert cause the gateway to think this is a different user connecting?