I've been contacted by a local golf course that has lost login access to their Windows 2003 server (suspected cause is a password change by a disgruntled ex-manager).
When I visited the site, they have the password taped to the wall behind the server and it had been working until a few weeks ago. When they try to login now it says incorrect username or password.
I've tried booting from the UBCD and running the Offline NT Password Editor application and it can see the hard drives (it's a RAID5) and the NTFS partition (DEV/SDA1), but when it tries to mount the partition, it fails with the error:
Failed to read last sector (sector number): invalid argument. etc etc. NTFS Probe returned error code 12. Sorry, cannot continue
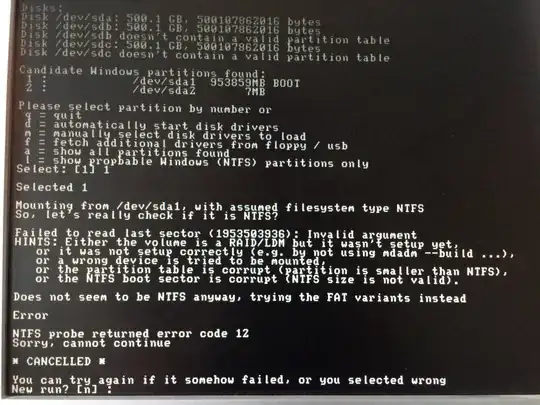
I'm assuming that it has loaded the correct RAID drivers given that it can see the HDD's and determine the partitions on the RAID volume. So what is causing this error?
Windows boots OK, but they can't log in. So surely it can't be an NTFS corruption... can it? From another computer on the network, they can log in using RDC but the account is not an administrative account so I can't reset any passwords or create a new Local admin account or an AD admin account.
I'd like to reset the Local admin password and/or the AD admin password. There appear to be a number of other user accounts in the Administrators group, so I'm waiting on the possible creators of those accounts to get back to us with possible passwords, but in regards to the actual "Administrator" account(s), what else can I try?