I am attempting to setup pfSense as a nat box for internal servers on a VPC.
I have followed the guides posted for configuring access and have followed the AWS instructions for setting up and configuring a nat instance but seem to still be missing something.
Here is a diagram to help convey what I'm trying to do:
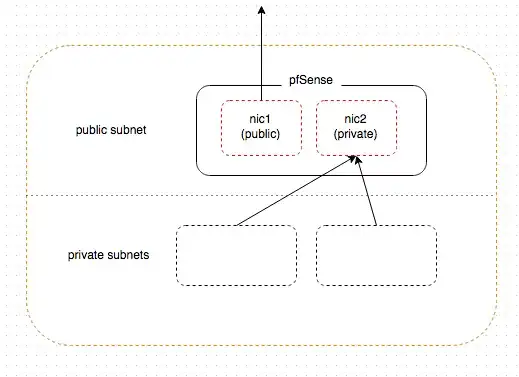
I think where I'm getting stuck is access to the second interface because I can ping the WAN interface but can't ping the secondary NIC I created. Both of the interfaces live in the "public" vpc subnet.
I'm not sure what to look at to get unstuck.
On the pfSense box I have the following outbound nat rule:
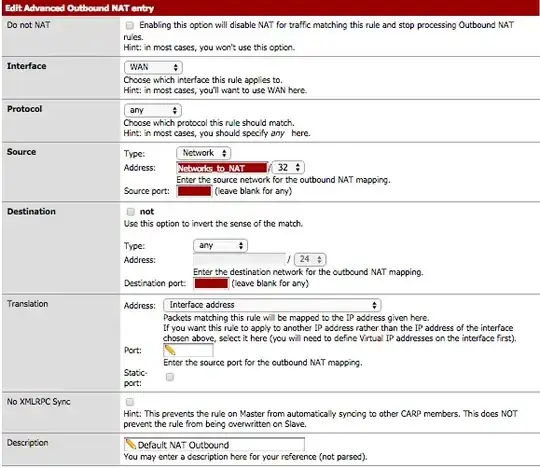
The alias contains the subnet that I am attempting to nat.
Maybe there is a way to configure the WAN interface to be the interface to NAT through and just not even bother with a secondary NIC? Let me know what other details are needed and I will update.