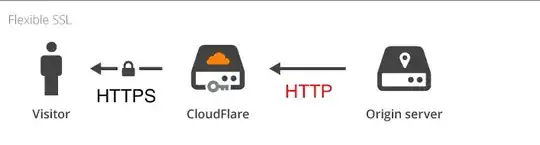
I am trying to implement Flexible SSL provided by CloudFlare to my site.
Here is my nginx config:
# PHP-FPM upstream; change it accordingly to your local config!
upstream php-fpm {
server 127.0.0.1:9000;
}
server {
listen 80;
server_name example.com www.example.com;
return 301 https://$server_name$request_uri;
}
server {
## Listen ports
listen 443;
# use _ if you want to accept everything, or replace _ with domain
server_name example.com www.example.com;
location / {
#proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X_FORWARDED_PROTO https;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header Host $http_host;
proxy_set_header X-Url-Scheme $scheme;
proxy_redirect off;
proxy_max_temp_file_size 0;
}
(...rest of config...)
However, when I try to connect to the website (Wordpress), I get a redirect loop (chrome: ERR_TOO_MANY_REDIRECTS). How do I configure nginx to prevent this?