Related to this previous question of mine about why it's a bad idea to use the root domain name as your Active Directory forest's name...
I have an employer, whom I will refer to as ITcluelessinc, for the purposes of simplicity (and honesty). This employer has an externally hosted website, www.ITcluelessinc.com, and a few Active Directory domains. Being clueless about IT, many years ago, they set themselves up on an Active Directory forest named ITcluelessinc.prv, and performed unspeakable atrocities against it. These unspeakable atrocities eventually caught up with them, and with everything collapsing around them, they decided to pay someone a huge chunk of money to "fix it ," which included migrating off the horribly broken ITcluelessinc.prv forest.
And of course, being clueless about IT, they didn't know good advice when they heard it, accepted the recommendation to name their new AD forest ITcluelessinc.com, instead of the sane advice they also got, and started putting stuff on it. Fast forward to a few hours ago, and we have a company with most of its stuff joined to and using the old ITcluelessinc.prv Active Directory forest, with a fair amount of newer stuff joined to and/or using the ITcluelessinc.com forest. To make this work together relatively seamlessly, I've used conditional forwarders in DNS to send the ITcluelessinc.com traffic over to ITcluelessinc.prv, and vice-versa.
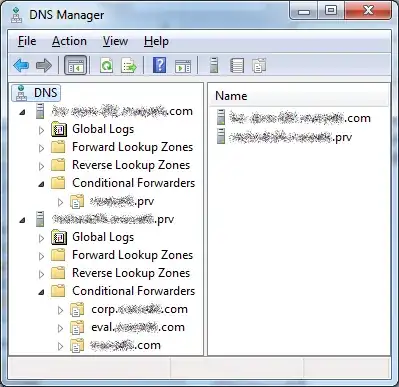
(The corp.ITcluelessinc.com and eval.ITcluelessinc.com domains are properly named domains I came in and set up later, and are not relevant just yet.)
Back to a few hours ago, and a non-technical employee of ITcluelessinc has noticed that she can't browse to www.ITcluelessinc.com from her workstation (inside the ITcluelessinc corporate network) and decided that this is a problem, so she contacts VIP employee of ITcluelessinc, who decides this must be resolved most Ricky-tick. Typically, not a huge deal, add an A record for www under the DNS zone for ITcluelessinc.com, and you can browse the site, so long as you don't try the naked link.
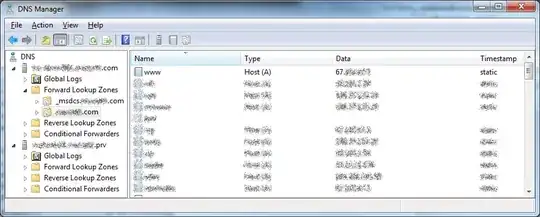
So, it seems like it's all setup properly. Forwarders, www host entry in DNS, and yet, clients using the ITcluelessinc.prv domain controller as DNS servers get a connection timeout when trying to browse to www.ITcluelessinc.com, instead of the webpage that I get from my home network.
Does anyone have any thoughts as to how I can allow internal clients of the ITcluelessinc.prv domain to browse www.ITcluelessinc.com, given the presence of the ITcluelessinc.com Active Directory forest and the conditional forwarders it needs? Or, alternately, is anyone [else] convinced that the only way to make it work is to get rid of the ITcluelessinc.com Active Directory forest?
It does seem like the setup I have now should work, but it's clearly not, and I have no idea where I'd procure a testing environment this messed up to experiment with. And for what it's worth, I've somewhat politely suggested that the only way to fix this is migrate to the properly-named forests I set up, and when that's not a good enough answer, plan to host a mirror of the website on all our ITcluelessinc.com domain controllers until that breaks everything.