My brain is a little bit fried trying to figure this out but I can't seem to get private subnets to connect to the internet to grab updates for example. Basically all I want is web access for these servers. I have tried solutions found in other posts but could easily be missing something since I have been looking at this for quite awhile.
So far I have done the following set up:
- Disable source/destination checking on my NAT instance
- Create a route table for public subnet and set its source to IGW (verified this works)
- Create a route table for private subnet and set its source to the NAT instance
- Create security group for NAT instance with inbound and outbound rules for 80/443 and ssh
- Create security group for private instance with inbound and outbound 80/443 and ssh
I am able to jump on the NAT instance via SSH and then pivot onto the private server, so I know that much is working. I have verified my rules by pinging internal addresses but when I leave the local network that is when I start having problems.
Where do I need to look or what do I need to troubleshoot to help get this narrowed down? Is there some configuration that needs to be done on the NAT instance that I have overlooked?
EDIT: Configuration update
- VPC: 172.16.0.0./16
- Private subnet: 172.16.1.0/24
- Public subnet: 172.16.0.0/24
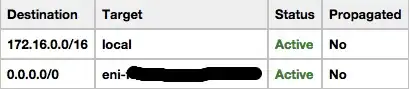
Private subnet routing table:
Points to NAT instance in public subnet. Unable to access internet, attached EIP to public internet facing interface.
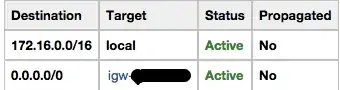
Public subnet routing table:
Points the public subnet at the IGW, I have verified internet access.
Thoughts:
I'm starting to think there is something that needs to be set up or created on the NAT instance that lives in the public subnet to forward traffic from private instances, but I'm not exactly sure what needs to added. I found this post that explains adding a masquerade rule in iptables, is that something that apply to my situation?