Is it possible on linux to have a whitelist of IP's that are allowed to reach a specific VM on the internal NAT? eg (public ip (proxmox) --> My VM for whitelisted IP's (192.168.0.1)), and if the traffic is not on the whitelist just route it to 192.168.0.2 ?
The problem is that a certain service is suffering from attacks, so I want users to register on a website before they can connect to the real deal. (and if anyone tries, they will connect to a dummy server on 192.168.0.2 which will catch all the attacks and display a message for users they need to register before connecting)
(if anyone needs visualization to make it easier, because maybe my storywriting skills aren't that good, here is a link: http://i.imgur.com/BCCkhmm.png)
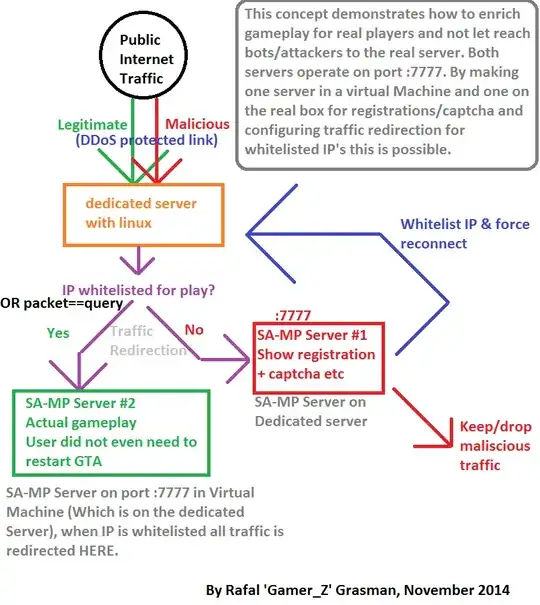
Additional question: Is it somehow possible for packets with a certain signature (for example QUERY packets) to be always allowed for any ip, even non whitelisted (redirect this traffic where whitelisted traffic goes)?