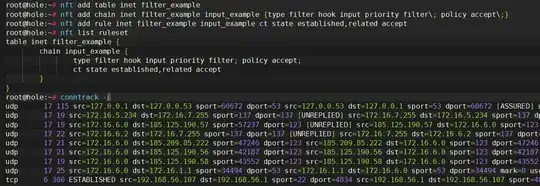
I tried the command conntrack -L and it returns nothing when I have a ping www.google.com running.
I also tried to load the module by modprobe nf_conntrack. But it still always returns conntrack v1.0.0 (conntrack-tools): 0 flow entries have been shown.
Any one know what would be the solution?