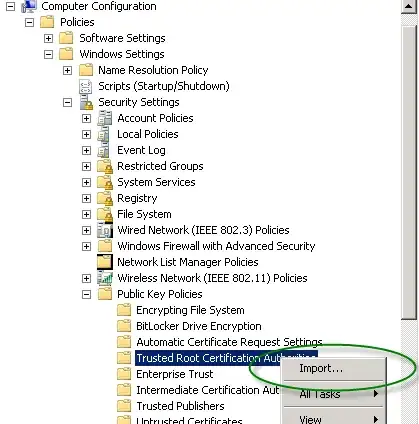
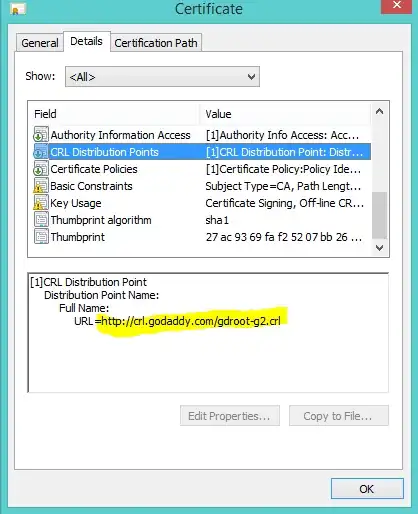
I'm trying to setup an AD server running the NPS service so that both AD and non-AD machines see the certificate as valid when authenticating to the wireless network. I picked up a cert from GoDaddy and the non-AD machines are happy with it, but the AD machine I'm testing with is complaining that it is not a valid certificate.
How do I configure NPS so that both AD members and non-AD members are happy with the certificate?
EDIT: I'm getting the error message mentioned here: http://support.microsoft.com/kb/2518158 "The server “” presented a valid certificate issued by “”, but “” is not configured as a valid trust anchor for this profile."
I'd rather not change all the AD clients to make this work. I'd prefer a solution that works by changing the server.