I am doing an implementation on a linux machine to reject incoming telnet requests from wan side telnet port 8023. The functionality is achieved by using the below iptables rules. The first rule in NAT prerouting chain to DNAT incoming tcp frames from port 8023 to 23, and the second rule to reject these tcp frames on port 23 with tcp-reset
iptables -t nat -A PREROUTING -i wan+ -p tcp --dport 8023 -j DNAT --to-destination :23
iptables -A INPUT -i wan+ -p tcp --dport 23 -j REJECT --reject-with tcp-reset
The new session on the wan machine gets terminated after adding these rules.
[root@ROOT ~]# telnet 192.168.3.252 8023
Trying 192.168.3.252...
Connected to 192.168.3.252.
Escape character is '^]'.
Connection closed by foreign host.
However, on seeing wireshark capture of the entire transaction from the wan machine, the following sequence has been observed.
TCP sequence:
SYN -->
<-- SYN/ACK
ACK -->
<-- RST
The wireshark capture has been attached too.
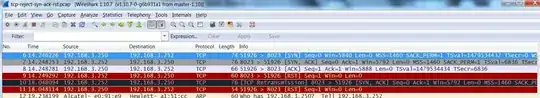
Can we send RST for the first SYN request by rule in iptables as below?
TCP sequence:
SYN -->
<-- RST
Could some one help in this regard... Thanks in advance.