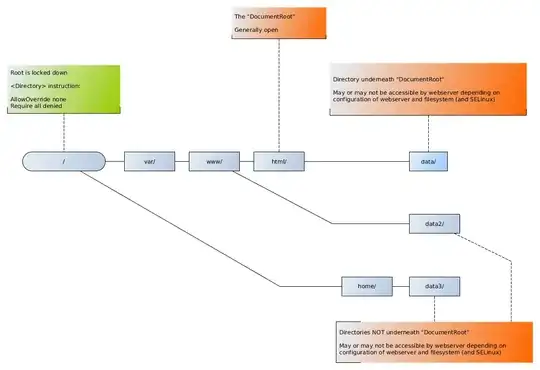
I have a general question about security of Apache DocumentRoot, which comes from a statement I read when installing Galaxy, a bioinformatic web service and infrastructure. The statement says
"Please note that Galaxy should never be located on disk inside Apache's DocumentRoot.
By default, this would expose all of Galaxy (including datasets) to anyone on the web."
This paragraph is copied from https://wiki.galaxyproject.org/Admin/Config/ApacheProxy
So the question is what's the difference between putting some contents in DocumentRoot vs putting in a sub-directory of DocumentRoot? Even if the contents are put in a sub-directory, by default, would it also be true that all the contents will be exposed to anyone on the web?
If I put the contents in DocumentRoot of an SSL server, and only allow authenticated and authorized users to access, would this resolve the world-wide access issue?
Update: Thank you all for your thoughtful answers. I think I had all my questions answered. To summarize:
A sub-directory in DocumentRoot will be accessible to everyone unless it has different permissions set.
SSL only protect the packets transferred over the networks, not the permission of the files.
Authentication/authorization will limit who can access DocumentRoot.
Unix/Linux file permissions won't affect the access as all files must be accessible by the web server owner.