Yes, it is possible. But the only good way that I can think of to do it using Active Directory is to modify the AD schema. Modifying the AD schema is one of those things that administrators shy away from doing because one, it is basically irreversible (by "irreversible" I mean without an authoritative restore) and two, making irreversible changes to a production Active Directory scares many administrators. If you were making an application or plugin, you would have to consider that your software would not be used by as many organizations if it required AD schema modification.
But modifying the AD schema is not bad thing per se, as long as we have a good reason for doing it. Installing Microsoft Exchange, for example, extends the AD schema. A lot.
We know that Active Directory is plenty capable of and well suited to storing this kind of data (user's public keys) because it already stores the X509 public keys for users if you use a PKI. But I would definitely not try to commandeer one of those existing attributes like X509-Cert or User-Cert or thumbnailPhoto to stuff your own custom data into it. That would cause problems if your organization ever wanted to use a PKI or other products that assumed that those AD attributes held the actual kind of data that they were designed to store.
There are plenty of existing user attributes that you can sneak your data into if your data is a very small string... description, employeeID, telexNumber, etc. But there are not many attributes that are suitable for storing a kilobyte or more of data. And those are usually already spoken for.
Nevertheless you can take a gander here and see if you can find an attribute that already exists on each user account that might be able to hold PGP public keys and not interfere with other applications:
Probably best that you create your own.
First, open Registry Editor on your schema master and edit:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Parameters
Schema Update Allowed (DWORD) 0x00000001
You do not have to reboot or even restart AD DS.
Next, register AD schema management snap-in:
regsvr32 schmmgmt.dll
Open MMC and add Active Directory schema snap-in.
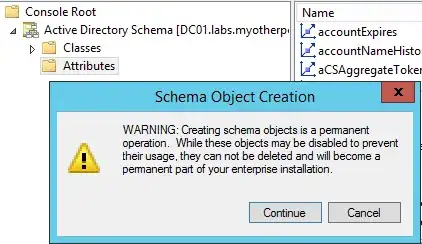
You have to assign an X500 object OID to your new attribute that is based on your domain's OID. You can use this script to generate a new X500 OID for your new schema attribute:
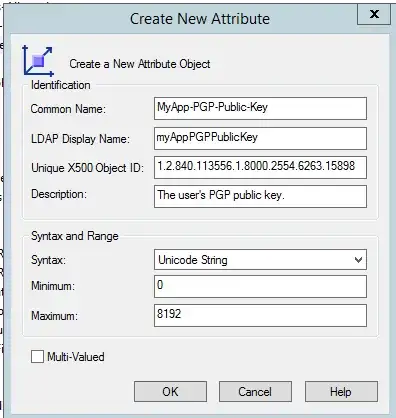
Notice that it's a good idea to prefix all your related attributes with an identical prefix, such as "MyApp". For instance, all the Active Directory specific attributes have a prefix like "msDS" and DFS Replication specific attributes will have a "msDFSR" prefix, etc. All future attributes that you add that are relevant to this software will use the same prefix and the same OID prefix.
You probably do not want to index this attribute, as searching for a user who has a specific PGP public key does not sound like a common search to me. (You only index things if you want to use them as search terms.) Or you might want to replicate to the global catalog if you have multiple domains in your forest. Beware that this can cause your indices and GC replication traffic increase substantially if you have a large domain.
Next you want to assign the new attribute to the Person class:
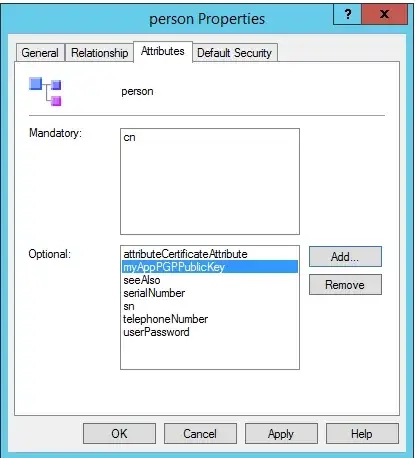
Now if you go check the Attribute Editor tab on your users, you will see that they have a new attribute for you to edit and query.
Some follow-up homework for you:
Edit the default security on the attribute so that only account owners (and maybe Domain Admins) can update the attribute on their own account and no one else's. This way, you can have your Outlook plugin automatically upload the PGP public key for the user assuming that their Outlook client is running under their security context.
Use a different syntax for your attribute. The Unicode String syntax that I used in my example sucks for something like a PGP key, but I was too lazy to go back and repeat everything just for you. :)


