I'll start by saying that I am no expert on the setup of servers. Far from it.
I am setting up an Ubuntu server with Apache running on ports 8080 and 4433 because another service on the server is using ports 80 and 443. I have modified the hosts file, the hostname file, provided the proper path to the certificates and have worked it down where there are no errors or warnings in the Apache error logs where certificates are concerned.
On my internal network I can access the named server (on ports 80 and 443) with no issue. On my internal network I can access the IP (internal using 192.168.nnn.nnn, on ports 8080 and 4433) with no issue. On my internal network I cannot even ping the external IP (using 69.1.nnn.nnn - I get no results.
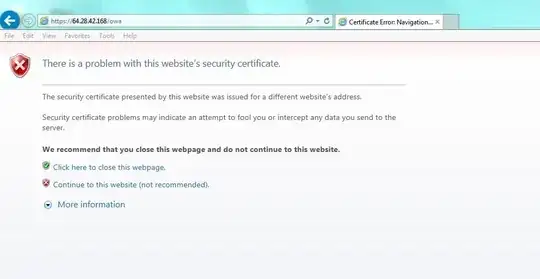
From outside of the network - I can access the named server (ports 80 / 443) with no issue. I cannot access the external IP (ports 80/ 443) without getting a distrusted certificate issue. Once I accept that there are issues with the cert it allows me proper access. I cannot access the external IP (ports 8080 / 4433) gateway timeout. I cannot access the external name server (ports 8080 / 4433) gateway timeout
I have been searching all day for a solution and I am willing to chalk it up to I have no idea what I am doing. Unfortunately I do not have anyone locally accessible (I've asked) who knows about this kind of thing.
From what I have written here is there anything obvious I have overlooked? Something in vhosts? Something the IT department has mis-configured in the firewall? I am at the end (and actually beyond - I learned some things) of my knowledge as this has gone beyond simple web server configuration.