I've just installed Windows Server 2008 on a server and I'm able to connect through Remote Desktop but can't ping. Do I need to open an special port on the firewall to be able to ping a server?
7 Answers
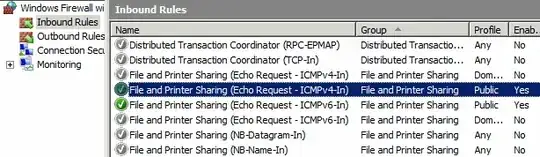
By default Windows 2008 does not respond to pings. To enable:
Administrative Tools
Windows Firewall with Advanced Security
Inbound Rules
File and Printer Sharing (Echo Request - ICMPv4-IN)
Enable Rule
You should now be able to ping your server from the LAN.
-
4What about IPv6? Won't someone please think of IPv6!?! – Mark Brackett May 08 '09 at 00:05
-
I can add that to allow ping from outside the subnet I had to enable "All profiles" for the rule, not only "public". – Zitrax Feb 13 '10 at 15:03
-
1Yeah. that is the most stupid goruping ever - File and printer sharing for ICMP ;) Got stumbled over that one, too ;) Everyone I tell that laughs. – TomTom Aug 17 '10 at 13:58
-
1What is more dumb is that the rule is disabled for the Domain profile, but enabled for Public and Private profiles. Surely most Domain profiles are on networks with a higher existing level of security than those you might deem Private or even Public... – dunxd Feb 08 '11 at 12:36
-
@MarkBrackett perhaps you are good by now. Nevertheless default Scope for this rule limits things to *Local subnet*. Change it to any, and you'd be able to ping with ICMPv6 you PC from outside your WAN. – mlt May 30 '15 at 05:36
Enable ping through the Windows Firewall at the command line like so:
netsh firewall set icmpsetting 8
Apparently this has changed in Windows Server 2008 R2 and newer, to:
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request"
protocol=icmpv4:8,any dir=in action=allow
That's.. uh... quite a mouthful.
- 12,994
- 20
- 74
- 92
-
http://technet.microsoft.com/en-us/library/cc737845(WS.10).aspx has the list of all the values, search for "set icmpsetting" within the page. – Luke Quinane Jun 24 '09 at 01:33
in powershell you can use :
# allow-icmp.ps1
# Sets up windows firewall to allow inbound ICMP - using PowerShell
# Thomas Lee - tfl@psp.co.uk
#create firewall manager object
$FWM=new-object -com hnetcfg.fwmgr
# Get current profile
$pro=$fwm.LocalPolicy.CurrentProfile
# Check Profile
if ($pro.IcmpSettings.AllowInboundEchoRequest) {
"Echo Request already allowed"
} else {
$pro.icmpsettings.AllowInboundEchoRequest=$true
}
# Display ICMP Settings
"Windows Firewall - current ICMP Settings:"
"-----------------------------------------"
$pro.icmpsettings
- 297
- 2
- 7
You will want to allow ICMP packets through. Ping doesn't use TCP, so there is no port to open.
- 8,748
- 1
- 27
- 39
-
7The fact that "ping doesn't use TCP" is a little misleading. Since there are other protocols that use ports, it's perhaps more useful to say "ping uses ICMP, which is a portless, layer-3 protocol, so you enable ICMP to allow ping, not open a port". Some firewalls allow you to filter message type, so you need to allow "echo request" and "echo response" to allow ping to work. – jj33 May 08 '09 at 02:05
-
er, "...to allow ping to work if you didn't want to otherwise allow all message types for some reason". – jj33 May 08 '09 at 02:06
Run these 2 in admin powershell, it enables both ipv6 and ipv4 inbound pings on all networks (public/private/domain):
Set-NetFirewallRule -DisplayName "File and Printer Sharing (Echo Request - ICMPv4-In)" -enabled True
Set-NetFirewallRule -DisplayName "File and Printer Sharing (Echo Request - ICMPv6-In)" -enabled True
It is equivalent to this https://serverfault.com/a/6049/147813
- 335
- 1
- 5
- 12
Another way of fixing this:
netsh advfirewall firewall add rule name="ICMP Allow incoming V4 echo request" protocol=icmpv4:8,any dir=in action=allow
- 17,761
- 6
- 62
- 81
- 355
- 1
- 4
- 16
-
While that works, it adds a rule, as opposed to enabling the 'baked in' rule. This could lead to confusion (the baked-in rule not being enabled, yet ICMP still working because of the added rule, when attempting to account-for or predict the FW behaviour). However, it could still be useful if you wanted to allow ICMP only for a particular network profile (eg. only for domain) since the baked-in rule targets all profiles. – David Bullock Jun 15 '21 at 01:22
Pay attention to use the correct quotation marks. Some web sites replace the quotation marks by similar symbols which cause syntax errors. C.f. enter link description here
- 141
- 1
- 1
- 5