I am installing Active Directory Lightweight Directory Services (AD LDS, aka ADAM) on a Windows 2012 vm. After finally getting the configuration of the directory and synchronization handled, I am now running into an interesting problem. I have researched online for hours already, and I could use some expert advice.
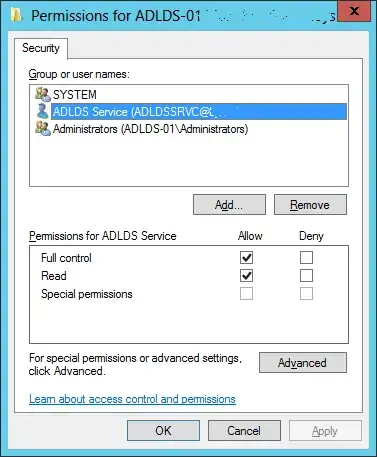
When I use "Network Service" account as the service account for my LDS instance, I cannot initiate a connection on the SSL port (which I left as the default of 636) at all. We can make connections to the non-SSL port of 389. The same occurs for the domain service account "ADLDSSRVC."
When I use my personal domain credentials as the service account, we can use non-SSL connections on the non-SSL port and SSL connections on the SSL port. On the SSL connection, we can then bind to the LDS using the AD DS accounts via proxy bind redirection. My domain account has local admin rights on the host.
Do I need to make the domain service account, "ADLDSSRVC" a local admin? My boss wants to do this only as a last resort if I can't give it just the permissions I need. More specifically, I would like to know, if it's possible, what permissions the service account needs so that I can make SSL ldap connections to my AD LDS instance. A Technet article indicates that the ADLDS service account needs create, read, and modify access to %ProgramFiles%\Microsoft ADAM\instancename\data, but that didn't seem to make a difference for opening up port 636.
Blog.uvm.edu tells to do the following: Open the AD Users and Computers tool, locate the computer object on which you installed the Instance. Give the LDS service account “create all child objects” to the computer object. I'm not a domain admin, so I can't do that. Is that basically the same as making the service account a local admin?