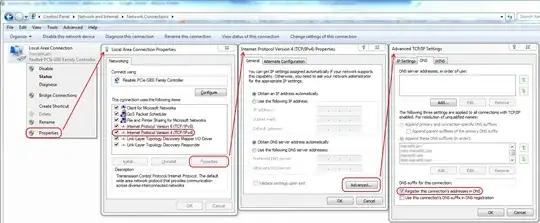
In our Windows AD domain, we have 2 DCs that also act as our DNS servers which allow the client computers to update their A records. We have a lot of outside salespeople, so some of our laptops have to go off-site for long periods of time and connect in through our (full tunnel) SSL VPN, using a Fortinet VPN client. DNS over the VPN tunnel works fine, VPN clients are able to resolve local hostnames perfectly.
The problem is that the clients connecting in over the VPN do not update the DNS records with their SSLVPN Adapter IP address. In fact, they don't update the DNS server at all. From my research, I've determined that clients are supposed to send an update to the DNS server "when a change occurs," but that doesn't seem to happen when the SSL VPN adapter connects and gets an IP address.
I have thought about deploying PowerShell scripts to all of the computers that employ the DNSCMD command when it detects that the SSL VPN adapter has an IP address, but that solution is far from ideal, feels overly complicated and very messy. I am hoping there is a simpler solution to this that I have not been able to dig up.